A particular joy of the Gemini and Spartan protocols – and the Markdown-like syntax of Gemtext – is their simplicity.
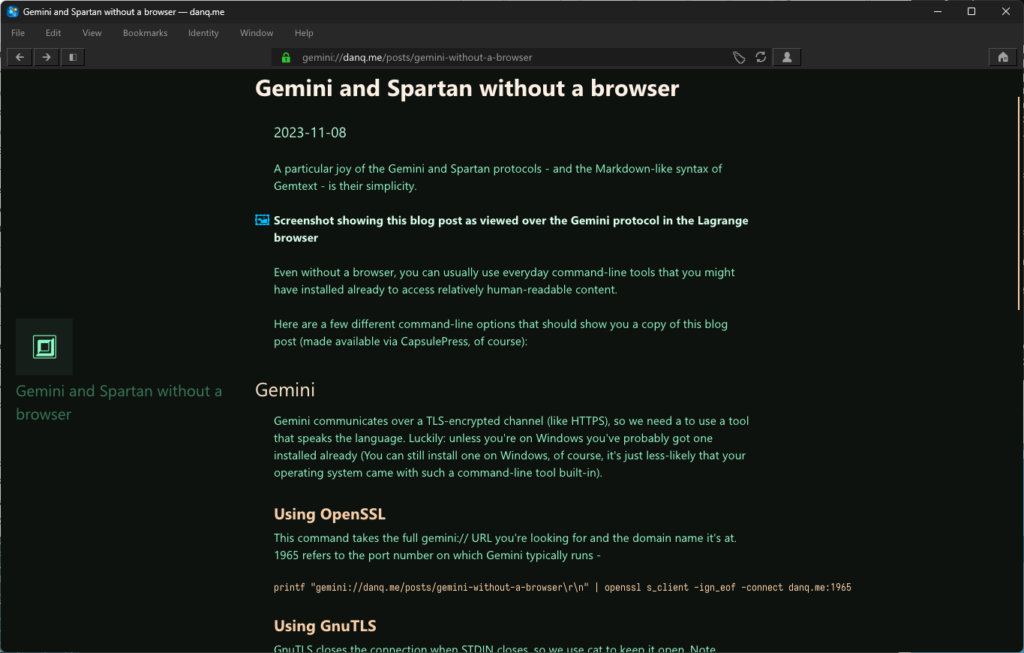
Even without a browser, you can usually use everyday command-line tools that you might have installed already to access relatively human-readable content.
Here are a few different command-line options that should show you a copy of this blog post (made available via CapsulePress, of course):
Gemini
Gemini communicates over a TLS-encrypted channel (like HTTPS), so we need a to use a tool that speaks the language. Luckily: unless you’re on Windows you’ve probably got one installed already1.
Using OpenSSL
This command takes the full gemini:// URL you’re looking for and the domain name it’s at. 1965 refers to the port number on which Gemini typically runs –
printf "gemini://danq.me/posts/gemini-without-a-browser\r\n" | \ openssl s_client -ign_eof -connect danq.me:1965
Using GnuTLS
GnuTLS closes the connection when STDIN closes, so we use cat to keep it open. Note inclusion of --no-ca-verification to allow self-signed
certificates (optionally add --tofu for trust-on-first-use support, per the spec).
{ printf "gemini://danq.me/posts/gemini-without-a-browser\r\n"; cat -; } | \
gnutls-cli --no-ca-verification danq.me:1965
Using Ncat
Netcat reimplementation Ncat makes Gemini requests easy:
printf "gemini://danq.me/posts/gemini-without-a-browser\r\n" | \ ncat --ssl danq.me 1965
Spartan
Spartan is a little like “Gemini without TLS“, but it sports an even-more-lightweight request format which makes it especially easy to fudge requests2.
Using Telnet
Note the use of cat to keep the connection open long enough to get a response, as we did for Gemini over GnuTLS.
{ printf "danq.me /posts/gemini-without-a-browser 0\r\n"; cat -; } | \
telnet danq.me 300
Using cURL
cURL supports the telnet protocol too, which means that it can be easily coerced into talking Spartan:
printf "danq.me /posts/gemini-without-a-browser 0\r\n" | \ curl telnet://danq.me:300
Using Ncat/Netcat
Because TLS support isn’t needed, this also works perfectly well with Netcat – just substitute nc/netcat or whatever your platform calls it in place of
ncat:
printf "danq.me /posts/gemini-without-a-browser 0\r\n" | \ ncat danq.me 300
I hope these examples are useful to somebody debugging their capsule, someday.
Footnotes
1 You can still install one on Windows, of course, it’s just less-likely that your operating system came with such a command-line tool built-in
2 Note that the domain and path are separated in a Spartan request and followed by the size of the request payload body: zero in all of my examples
Fetching a website or API over telnet is a useful excercise for new web developers. It seems like almost all successful protocols are just text commands once you strip off encryption.
@Spencer: 100%. I have fond memories of working this out during my first reading of the (then just-published!) HTTP/1.1 RFC and seeing what else I could pull off with what was functionally just a telnet client that was smart enough to turn off its terminal emulation negotiation features! FTP, IRC, SMTP, Gopher… all highly accessible over telnet.
It pleases me a lot that, thanks to HTTP’s backwards-compatibility (I’m yet to see a HTTP/2 or HTTP/3 webserver that rejects connections that fail to upgrade protocol, but it might happen on some sad day), developers can still go through this rite of passage today. And that tools like ncat make the otherwise-hard part – the SSL/TLS layer- so lightweight and simple!
(I also routinely appreciate that nginx can detect http connections attempted to https ports and respond appropriately: that’s a really cool and underappreciated feature of my favourite web server!)