This checkin to geohash 2024-10-22 51 -1 reflects a geohashing expedition. See more of Dan's hash logs.
Location
Harcourt Hill Bridleway, between Cumnor and North Hinksey
Participants
Plans
I’m on sabbatical from work right now, so I’m hoping to be able to get out to this hashpoint while the kids are at school.
Expedition
After dropping the kids off at school, the geopup/hashhound and I set out for the hashpoint. Coming up the “short side” of the bridleway from Botley would be a shorter walk, but we opted to park in Cumnor and come up the “long side” of Harcourt Hill to avoid Oxford’s traffic (and the inevitable fee for parking on the city’s side of the hill).
Harcourt Hill (like my village of Stanton Harcourt) doubtless gets its name from the Harcourt Family, who supported William the Conqueror during his conquest of Great Britain back in 1066 and were ultimately granted huge swathes of land around this part of the world in recognition of their loyalty. To this day, you find “Harcourt” in a lot of place names in this neck of the woods.
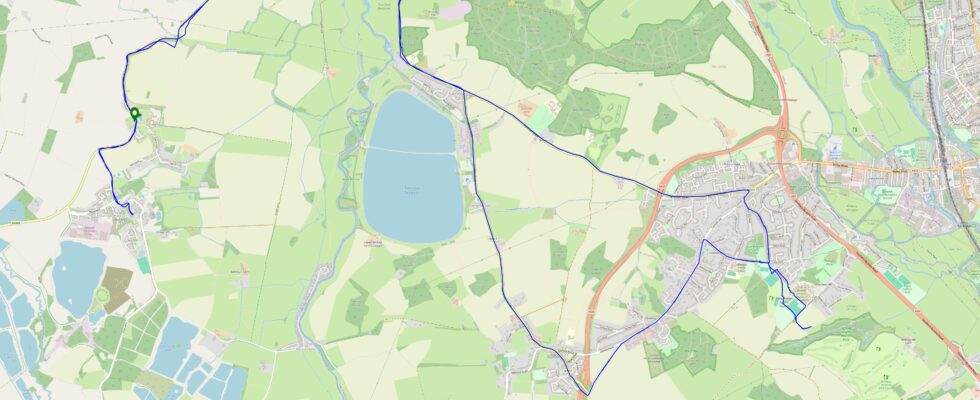
The hashpoint was so easy to find, we almost walked right over it: it’s right in the centre of the footpath/bridleway. Even my dog, who often doesn’t like long walks or muddy paths, didn’t get a chance to complain before we got there. We arrived at 09:35 and took the requisite photos, which can be found below. We also kept a GPS tracklog and vlogged our experience, all of which you can see below.
I’ve not properly hashed in a long while, so it was great to get back out there!
Tracklog
My GPSr kept a tracklog.
Video
Also available via YouTube.
Photos