Well this is a sight to wake up to. 😍
Tag: work
Note #24643
Pack Light
Think I blew Ruth‘s mind this morning when I set off for a week in Mexico with only a medium-sized, underseat-suitable backpack.
But since working for Automattic five years ago I’ve totally been bitten by the travelling-light bug. Highly recommended!
We’ll Pay You to Go (so we’re confident in who stays…)
This week has been a wild ride at Automattic. I’ve shared my take on our recent drama already1.
Off the back of all of this, our CEO Matt Mullenweg realised:
…
It became clear a good chunk of my Automattic colleagues disagreed with me and our actions.
So we decided to design the most generous buy-out package possible, we called it an Alignment Offer: if you resigned before 20:00 UTC on Thursday, October 3, 2024, you would receive $30,000 or six months of salary, whichever is higher.
…
HR added some extra details to sweeten the deal; we wanted to make it as enticing as possible.
I’ve been asking people to vote with their wallet a lot recently, and this is another example!
…
This was a really bold move, and gave many people I know pause for consideration. “Quit today, and we’ll pay you six months salary,” could be a pretty high-value deal for some people, and it was offered basically without further restriction2.
A 2008 Havard Business Review article (unpaywalled version) talked about a curious business strategy undertaken by shoe company Zappos:
…
Every so often, though, I spend time with a company that is so original in its strategy, so determined in its execution, and so transparent in its thinking, that it makes my head spin. Zappos is one of those companies
…
It’s a hard job, answering phones and talking to customers for hours at a time. So when Zappos hires new employees, it provides a four-week training period that immerses them in the company’s strategy, culture, and obsession with customers. People get paid their full salary during this period.
After a week or so in this immersive experience, though, it’s time for what Zappos calls “The Offer.” The fast-growing company, which works hard to recruit people to join, says to its newest employees: “If you quit today, we will pay you for the amount of time you’ve worked, plus we will offer you a $1,000 bonus.” Zappos actually bribes its new employees to quit!
…
I’m sure you can see the parallel. What Zappos do routinely and Automattic did this week have a similar outcome
By reducing – not quite removing – the financial incentive to remain, they aim to filter their employees down to only those whose reason for being there is that they believe in what the company does3. They’re trading money for idealism.
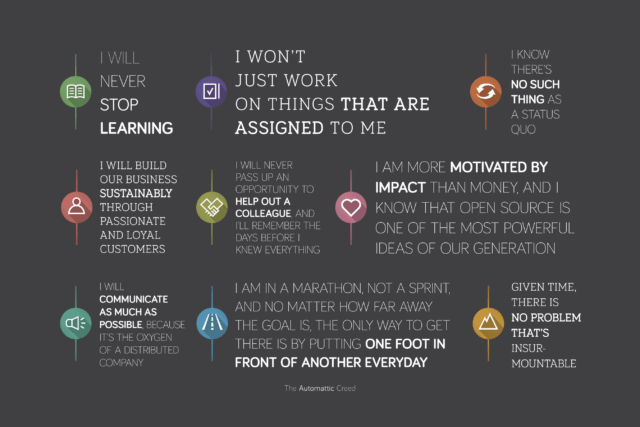
Buried about half way through the Creed is the line I am more motivated by impact than money, which seems quite fitting. Automattic has always been an idealistic company. This filtering effort helps validate that.
The effect of Automattic’s “if you don’t feel aligned with us, we’ll pay you to leave” offer has been significant: around 159 people – 8.4% of the company – resigned this week. At very short notice, dozens of people I know and have worked with… disappeared from my immediate radar. It’s been… a lot.
I chose to stay. I still believe in Automattic’s mission, and I love my work and the people I do it with. But man… it makes you second-guess yourself when people you know, and respect, and love, and agree with on so many things decide to take a deal like this and… quit4.

(These numbers are my own estimation and might not be entirely accurate.)
There’ve been some real heart-in-throat moments. A close colleague of mine started a message in a way that made me briefly panic that this was a goodbye, and it took until half way through that I realised it was the opposite and I was able to start breathing again.
But I’m hopeful and optimistic that we’ll find our feet, rally our teams, win our battles, and redouble our efforts to make the Web a better place, democratise publishing (and eCommerce!), and do it all with a commitment to open source. There’s tears today, but someday there’ll be happiness again.
Footnotes
1 For which the Internet quickly made me regret my choices, delivering a barrage of personal attacks and straw man arguments, but I was grateful for the people who engaged in meaningful discourse.
2 For example, you could even opt to take the deal if you were on a performance improvement plan, or if you were in your first week of work! If use these examples because I’m pretty confident that both of them occurred.
3 Of course, such a strategy can never be 100% effective, because people’s reasons for remaining with an employer are as diverse as people are.
4 Of course their reasons for leaving are as diverse and multifaceted as others’ reasons for staying might be! I’ve a colleague who spent some time mulling it over not because he isn’t happy working here but because he was close to retirement, for example.
Note #24599
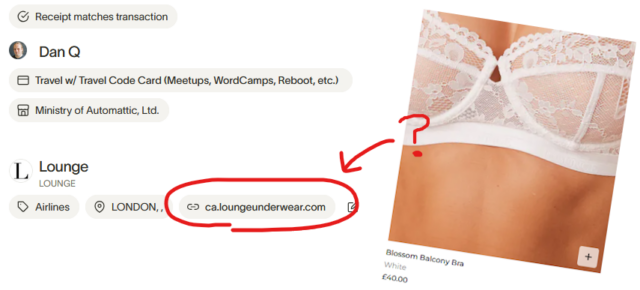
At work, we recently switched expenses system to one with virtual credit card functionality. I decided to test it out by buying myself lounge access for my upcoming work trip to Mexico. Unfortunately the new system mis-detected my lounge access as being a purchase from lingerie company loungeunderwear.com. I’m expecting a ping from Finance any moment to ask me why I’m using a company credit card to buy a bra.
One might ask why our expenses provider can (mis-)identify loungeunderwear.com from a transaction in the first place. Did somebody at some company that uses this provider actually buy some ladies’ briefs on a company credit card at some point?
Idea: Meeting Spoofer
Focus time is great
I’m a big fan of blocking out uninterrupted time on your work calendar for focus activities, even if you don’t have a specific focus task to fill them with.
It can be enough to simple know that, for example, you’ve got a 2-hour slot every Friday morning that you can dedicate to whatever focus-demanding task you’ve got that week, whether it’s a deep debugging session, self-guided training and development activities, or finally finishing that paper that’s just slightly lower priority than everything else on your plate.
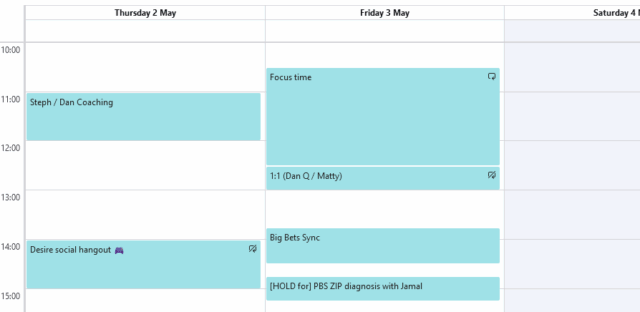
I appreciate that my colleagues respect that blocked period: I almost never receive meeting requests in that time. That’s probably because most people, particularly because we’re in such a multi-timezone company, use their calendar’s “find a suitable time for everybody” tool to find the best time for everyone and it sees that I’m “busy” and doesn’t suggest it.
If somebody does schedule a meeting that clashes with that block then, well, it’s probably pretty urgent!
But it turns out this strategy doesn’t work for everybody:
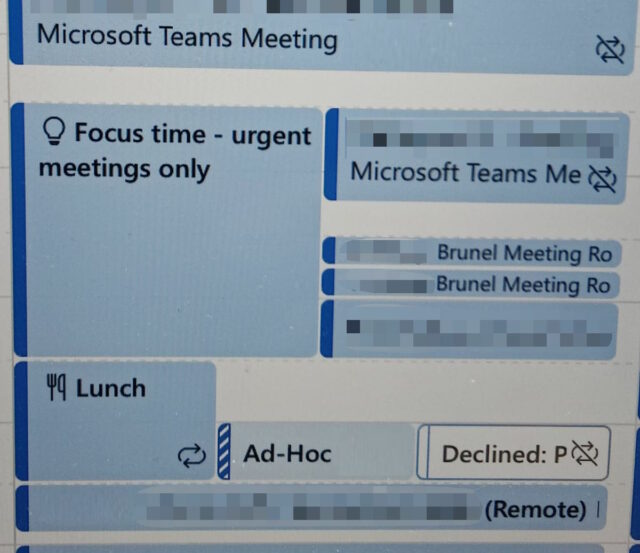
My partner recently showed me a portion of her calendar, observing that her scheduled focus time had been overshadowed by four subsequently-created meetings that clashed with it. Four!
Maybe that’s an exception and this particular occasion really did call for a stack of back-to-back urgent meetings. Maybe everything was on fire. But whether or not this particular occasion is representative for my partner, I’ve spoken to other friends who express the same experience: if they block out explicit non-meeting time on their calendar, they get meeting requests for that time anyway. At many employers, “focus time” activities don’t seem to be widely-respected.
Maybe your workplace is the same. The correct solution probably involves a cultural shift: a company-wide declaration in favour of focus time as a valuable productivity tool (which it is), possibly coupled with recommendations about how to schedule them sensitively, e.g. perhaps recommending a couple of periods in which they ought to be scheduled.
But for a moment, let’s consider a different option:
A silly solution?
Does your work culture doesn’t respect scheduled focus time but does respect scheduled meetings? This might seem to be the case in the picture above: note that the meetings that clash with the focus time don’t clash with one another but tessellate nicely. Perhaps you need… fake meetings.
Of course, creating fake meetings just so you can get some work done is actually creating more work. Wouldn’t it be better if there were some kind of service that could do it for you?
Here’s the idea: a web service that exposes an API endpoint. You start by specifying a few things about the calendar you’d like to fill, for example:
- What days/times you’d like to fill with “focus time”?
- What industry you work in, to help making convincing (but generic) event names?
- Whether you’d like the entire block consistently filled, or occasional small-but-useless gaps of up to 15 minutes inserted between them?
This results in a URL containing those parameters. Accessing that URL yields an iCalendar feed containing those meetings. All you need to do is get your calendar software to subscribe to those events and they’ll appear in your calendar, “filling” your time.
So long as your iCalendar feed subscription refreshes often enough, you could even have an option to enable the events to self-delete e.g. 15 minutes before their start time, so that you don’t panic when your meeting notification pops up right before they “start”!
This is the bit where you’re expecting me to tell you I made a thing
Normally, you’d expect me to pull the covers off some hilarious domain name I’ve chosen and reveal exactly the service I describe, but I’m not doing that today. There’s a few reasons for that:

- Firstly, I’ve got
enoughtoo many pointless personal/side projects on the go already1. I don’t need another distraction. - Secondly, it turns out others have already done 90% of the work. This open-source project runs locally and fills calendars with (unnamed, private) blocks of varying lengths. This iOS app does almost exactly what I described, albeit in an ad-hoc rather than fully-automated way. There’s no point me just doing the last 10% just to make a joke work.
- And thirdly: while I searched for existing tools I discovered a significant number of people who confess online to creating fake meetings in their calendars! While some of these do so for reasons like those I describe – i.e. to block out time and get more work done in an environment that doesn’t respect them simply blocking-out time – a lot of folks admit to doing it just to “look busy”. That could be either the employee slacking off, or perhaps having to work around a manager with a presenteeism/input-measurement based outlook (which is a terrible way to manage people). But either way: it’s a depressing reason to write software.
Nope
So yeah: I’m not going down that avenue.
But maybe if you’re in a field where you’d benefit from it, try blocking out some focus time in your calendar. I think it’s a fantastic idea, and I love that I’m employed somewhere that I can do so and it works out.
Or if you’ve tried that and discovered that your workplace culture doesn’t respect it – if colleagues routinely book meetings into reserved spaces – maybe you should try fake meetings and see if they’re any better-respected. But I’m afraid I can’t help you with that.
Footnotes
1 Consider, for example, how I’m trying to take a photo of my dog, with her tongue stuck out, every day of this month.
Dan Q found GC4MHJ0 Octo (MK Artwalks)
This checkin to GC4MHJ0 Octo (MK Artwalks) reflects a geocaching.com log entry. See more of Dan's cache logs.
Today’s the last of three consecutive days that I’ve spent working in Milton Keynes. On each day I’ve taken a short walk while I’ve eaten my lunch to find a nearby geocache. This was today’s.
After admiring the sculpture I snapped a selfie while I waited for my GPS signal to settle. The coordinates and the hint made the location seem obvious, yet somehow I did three laps of the hiding place before I reached down to what by all accounts was, indeed, an obvious hiding place!
Muggles weren’t too multitudinous, so I soon had the cache hidden again back in its snug little spot. TFTC!
Dan Q found GC2GR3Z The Brass Bands of MK – Secklow Brass
This checkin to GC2GR3Z The Brass Bands of MK - Secklow Brass reflects a geocaching.com log entry. See more of Dan's cache logs.
I’ve been working in Milton Keynes the tail end of this week while my kids attend a ski camp at the X-scape centre. While eating my lunch today I came out for a walk to find this geocache.
Approaching from the direction of the car park was definitely the right route and I was soon standing at GZ alongside a likely host. I had to search for some time, though, before I found this surprisingly we’ll-concealed cache.
(I was hindered perhaps by my own eagerness to check the hint, which left me searching several feet lower down than the container eventually turned out to be!)
Right, back to work for me! TFTC.
Note #24370
The Sprint Plan And The Noise
Power’s out yet again at my house (though not for the last reason nor because of our weird wiring: this time it’s for tree trimming), so here I am in my favourite coworking-friendly local cafe with The Signal And The Noise (which I’ve talked about before) in my ears and a whole lot of sprint planning at my fingertips.
Suno the Cheerleader
I continue to be sceptical of AI‘s ability to solve 90%+ of the problems that people are trying to solve with it.
But damn, if you’re feeling uninspired as you’re getting ready to start work on a Monday morning, try dumping your to-do list into a songwriting AI like Suno and ask it to write an uplifting song about how you’ll get it finished. It’s like having your very own cheerleader.
❎ Good ❎ Cheap ☑️ Fast. I guess generative AI is a “choose one” situation, and the one you have to choose is “fast”. But still: it certainly got me pumped-up and ready to work.
Also available on:
Generation details
Prompt: uplifting electronic pop about Dan completing his to-do list today: filing his meetup expenses; performance-testing his CircleCI workflow; leading a team meeting; learning about Full Site Editing
Lyrics:
Filing expenses
Gotta get ’em done
No time to waste
Gotta have some fun
Dan’s on a mission
Gotta stay on track
He’s gonna conquer
Ain’t nothing gonna hold him back
Performance testing
Gonna make it fly
CircleCI workflow
Gonna reach the sky
Dan’s got the focus
He’s in the zone
Gonna make it happen
Gonna make it his own
Leading that team meeting
Gonna show his might
Guiding them forward
Shining so bright
Dan’s a leader
He’s got it all
Inspiring the team
Gonna make ’em stand tall
Window Tax
Podcast Version
This post is also available as a podcast. Listen here, download for later, or subscribe wherever you consume podcasts.
…in England and Wales
From 1696 until 1851 a “window tax” was imposed in England and Wales1. Sort-of a precursor to property taxes like council tax today, it used an estimate of the value of a property as an indicator of the wealth of its occupants: counting the number of windows provided the mechanism for assessment.
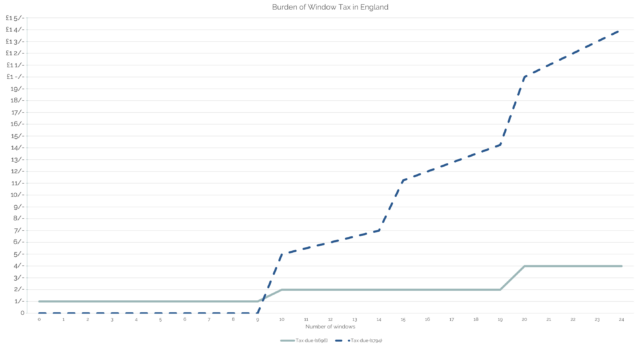
(A particular problem with window tax as enacted is that its “stepping”, which was designed to weigh particularly heavily on the rich with their large houses, was that it similarly weighed heavily on large multi-tenant buildings, whose landlord would pass on those disproportionate costs to their tenants!)

Why a window tax? There’s two ways to answer that:
- A window tax – and a hearth tax, for that matter – can be assessed without the necessity of the taxpayer to disclose their income. Income tax, nowadays the most-significant form of taxation in the UK, was long considered to be too much of an invasion upon personal privacy3.
- But compared to a hearth tax, it can be validated from outside the property. Counting people in a property in an era before solid recordkeeping is hard. Counting hearths is easier… so long as you can get inside the property. Counting windows is easier still and can be done completely from the outside!

…in the Netherlands
I recently got back from a trip to Amsterdam to meet my new work team and get to know them better.
One of the things I learned while on this trip was that the Netherlands, too, had a window tax for a time. But there’s an interesting difference.
The Dutch window tax was introduced during the French occupation, under Napoleon, in 1810 – already much later than its equivalent in England – and continued even after he was ousted and well into the late 19th century. And that leads to a really interesting social side-effect.

Glass manufacturing technique evolved rapidly during the 19th century. At the start of the century, when England’s window tax law was in full swing, glass panes were typically made using the crown glass process: a bauble of glass would be spun until centrifugal force stretched it out into a wide disk, getting thinner towards its edge.
The very edge pieces of crown glass were cut into triangles for use in leaded glass, with any useless offcuts recycled; the next-innermost pieces were the thinnest and clearest, and fetched the highest price for use as windows. By the time you reached the centre you had a thick, often-swirly piece of glass that couldn’t be sold for a high price: you still sometimes find this kind among the leaded glass in particularly old pub windows5.

As the 19th century wore on, cylinder glass became the norm. This is produced by making an iron cylinder as a mould, blowing glass into it, and then carefully un-rolling the cylinder while the glass is still viscous to form a reasonably-even and flat sheet. Compared to spun glass, this approach makes it possible to make larger window panes. Also: it scales more-easily to industrialisation, reducing the cost of glass.
The Dutch window tax survived into the era of large plate glass, and this lead to an interesting phenomenon: rather than have lots of windows, which would be expensive, late-19th century buildings were constructed with windows that were as large as possible to maximise the ratio of the amount of light they let in to the amount of tax for which they were liable6.

That’s an architectural trend you can still see in Amsterdam (and elsewhere in Holland) today. Even where buildings are renovated or newly-constructed, they tend – or are required by preservation orders – to mirror the buildings they neighbour, which influences architectural decisions.

It’s really interesting to see the different architectural choices produced in two different cities as a side-effect of fundamentally the same economic choice, resulting from slightly different starting conditions in each (a half-century gap and a land shortage in one). While Britain got fewer windows, the Netherlands got bigger windows, and you can still see the effects today.
…and social status
But there’s another interesting this about this relatively-recent window tax, and that’s about how people broadcast their social status.

In some of the traditionally-wealthiest parts of Amsterdam, you’ll find houses with more windows than you’d expect. In the photo above, notice:
- How the window density of the central white building is about twice that of the similar-width building on the left,
- That a mostly-decorative window has been installed above the front door, adorned with a decorative leaded glass pattern, and
- At the bottom of the building, below the front door (up the stairs), that a full set of windows has been provided even for the below-ground servants quarters!
When it was first constructed, this building may have been considered especially ostentatious. Its original owners deliberately requested that it be built in a way that would attract a higher tax bill than would generally have been considered necessary in the city, at the time. The house stood out as a status symbol, like shiny jewellery, fashionable clothes, or a classy car might today.

Can we bring back 19th-century Dutch social status telegraphing, please?9
Footnotes
1 Following the Treaty of Union the window tax was also applied in Scotland, but Scotland’s a whole other legal beast that I’m going to quietly ignore for now because it doesn’t really have any bearing on this story.
2 The second-hardest thing about retrospectively graphing the cost of window tax is finding a reliable source for the rates. I used an archived copy of a guru site about Wolverhampton history.
3 Even relatively-recently, the argument that income tax might be repealed as incompatible with British values shows up in political debate. Towards the end of the 19th century, Prime Ministers Disraeli and Gladstone could be relied upon to agree with one another on almost nothing, but both men spoke at length about their desire to abolish income tax, even setting out plans to phase it out… before having to cancel those plans when some financial emergency showed up. Turns out it’s hard to get rid of.
4 There are, of course, other potential reasons for bricked-up windows – even aesthetic ones – but a bit of a giveaway is if the bricking-up reduces the number of original windows to 6, 9, 14 or 19, which are thesholds at which the savings gained by bricking-up are the greatest.
5 You’ve probably heard about how glass remains partially-liquid forever and how this explains why old windows are often thicker at the bottom. You’ve probably also already had it explained to you that this is complete bullshit. I only mention it here to preempt any discussion in the comments.
6 This is even more-pronounced in cities like Amsterdam where a width/frontage tax forced buildings to be as tall and narrow and as close to their neighbours as possible, further limiting opportunities for access to natural light.
7 Yet I’m willing to learn a surprising amount about Dutch tax law of the 19th century. Go figure.
8 Obligatory Pet Shop Boys video link. Can that be a thing please?
9 But definitely not 17th-century Dutch social status telegraphing, please. That shit was bonkers.
Dan Q found GC89T04 Japanse glazen dobbers
This checkin to GC89T04 Japanse glazen dobbers reflects a geocaching.com log entry. See more of Dan's cache logs.
An easy find. Didn’t take nor leave any books, but briefly skimmed the Borland JBuilder 2 Getting Started guide, because it was familiar/nostalgic. Pretty sure I used this tool… about 25 years ago!
Dan Q found GC8R0FY SIX on the beach
This checkin to GC8R0FY SIX on the beach reflects a geocaching.com log entry. See more of Dan's cache logs.
An easy find. As a approached I thought that a couple cuddling here might be in my way, but they were just getting ready to leave as I arrived! SL (love the long thin logbook!), TFTC. Now to make my way back to the station!
Dan Q found GC79PX6 Galgenveld / Field of Gallows
This checkin to GC79PX6 Galgenveld / Field of Gallows reflects a geocaching.com log entry. See more of Dan's cache logs.
Eww. Had to put my hand into two gross holes before finding the (correct) third gross hole I needed to put my hand into. Worth it in the end for a happy smiley face. Thanks for bringing me to this place and teaching me its history. TFTC!