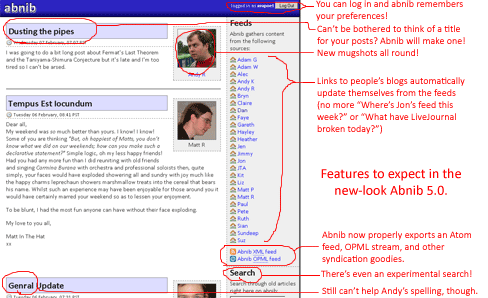
There’s a new version out: click here!
My previous post reminded me that I’d never gotten around to writing something I’d promised a few of you already: that is, a guide to using Google Reader and LiveJournal together effectively (Google Reader doesn’t support digest authentication, which means that it’s not possible to use Google Reader to pick up, for example, “friends only” posts, so I’ve written a bit of software that bridges the gap).
I’ve used a number of bits of newsreading software over the years before realising that what I really needed was a web-based reader that I could use from “wherever.” I implemented my own, Dog, which worked adequately, but Google Reader has since matured into a wonderful program, and it seemed a waste not to use it.
In case there’s anybody else out there in Abnibland who wants to be able to use Google Reader to centralise all their blog reading into one place and who has LiveJournal friends who make “friends only” posts (it’s nice to have all the comics I read, all the news I’m interested in, and all of the blogs I follow – including those on LiveJournal – integrated into one place with reminders when new stuff appears, searching, etc.), here’s my guide:
Google Reader For LiveJournal Users
- You’ll need a Google Reader account – if you’ve got some other kind of Google account (e.g. GMail), just log in, otherwise, sign up for one.
- You’ll also need one or more LiveJournal accounts through which you can read the “friends only” posts you’re interested in. Another advantage of this system is that if you have multiple LiveJournal identities you can read the blogs of the friends of both in one place. If you don’t have a LiveJournal account, why are you bothering with this guide? Just go use Google Reader itself like a normal person.
- Log in to LiveJournal Feed Fetcher using your LiveJournal username and password. Then, just click on each of the “Add To Google” buttons in turn for each of the friends whose blogs you’d like to syndicate.
- Remember to add other people’s (non LiveJournal) blogs to your Google Reader account, too!
Now, whenever you log in to Google Reader, you’ll be presented with the latest blog entries from all of the blogs you read, including “friends only” posts, if available, from your LiveJournal buddies.
Advanced Tips
- Install the Google Reader Notifier plugin (mirror) for Firefox. This sits in the bottom-right corner of your browser window and lets you know how many new posts you’ve got to read, and provides a convenient shortcut to your Google Reader account.
- In Google Reader, click Settings, then Goodies. Under “Put Reader in a bookmark” you’ll find a bookmarklet that you can drag to your Firefox Bookmarks Toolbar (or a similar place on the user interface). This will appear by default as a “Next” link that you can click to immediately go to the web page of the next item in your reading list.
I hope this short guide will reduce the demand for further maintenance of abnib help people to get a handle on Google Reader and on reading syndicated LiveJournal blogs. The LiveJournal Feed Fetcher can very be easily extended to cope with similar systems (DeadJournal, etc.), so just let me know if there’s anything it’s “missing.”
 In order to reduce the
amount of time my blog spends being used to organise events like Black Red Dwarf Adder Nights and whatnot, I’ve launched
In order to reduce the
amount of time my blog spends being used to organise events like Black Red Dwarf Adder Nights and whatnot, I’ve launched