Every year the Students Union here in Aberystwyth puts on the May Ball, an excuse to dress up and party
if ever I saw one, for students. For the last few years this has been held on-campus, in the Arts Centre, Students Union, and the
concourse in-between the two. Live music and shows, dancing, and a fairground… and hundreds of students in ball gowns and tuxedos… Since the event had been moved “on campus” there have
been less tickets available than ever, and demand grows steadily higher. As a result, students queue for hours to get their tickets.
This year, tickets began to be served at 10am, but the queue was 270 people long by forming by midnight: yes, people were willing to stand, all night, for ten hours, to be first in a
queue for May Ball tickets. The Students Union have, of course, monopolised on the situation and will be selling drinks to the people queuing. Hey; let’s charge them twice.
Another recent problem has been that of ticket touting. Tickets sell for under £40, but can be re-sold to those desperate to go for as much as £100. Last year, the Students Union would
not allow more than 8 tickets to be bought in a single transaction (and with queues so long, there’s no chance of queuing again), but that still meant that sly touts could easily earn
up to £480 for a few hours work. This year, only four tickets can be bought by any single person, but this simply resulted in a longer queue, sooner, and I don’t think it’ll stop
touting (if I was going to the May Ball, and therefore needed to queue anyway, I would buy my full allotted four tickets, regardless of how many people I was actually purchasing tickets
for… and I know of dozens of others who follow this methodology every year, meaning that even as demand goes up, the touts take an even larger share of the profits).
Thankfully, I’ve been to the May Ball once and I’ll happily get by without ever going again. But I got to thinking, having seen the lunacy in those students who’ve spent all of this
morning and all of last night queueing, that this isn’t the best way to be arranging this event…
A Better Way
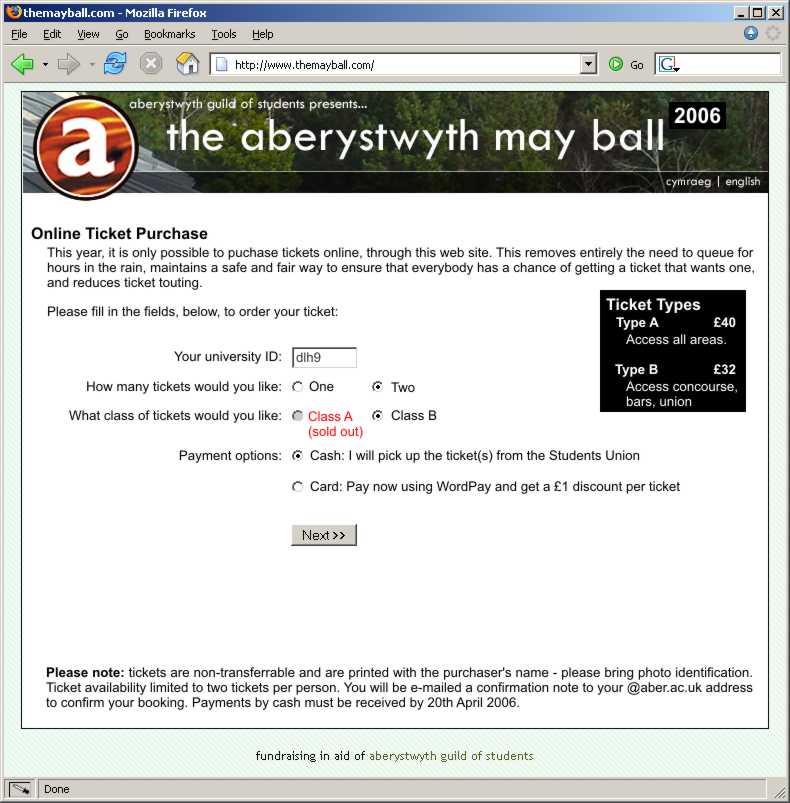
Here’s how it should be done. All the tickets should be sold online, by the Students Union. If you want to buy tickets, you connect to their web site and fill in the following details:
- Your university user name – this ensures that your ticket is ‘reserved’ for you, and that you cannot buy multiple tickets.
- The number and type of tickets you want to buy – only two tickets maximum per person.
- How you’d like to pay and obtain the tickets: you can pay online (and have them posted to you) or you can collect them from the union building for up to a week afterwards and pay in
cash.
An e-mail is sent to your university e-mail address to confirm that it really was you who ordered the tickets (and not somebody ordering in your name). If this is not replied to within
24 hours (as will be explained in the e-mail), the order is cancelled. The tickets (which are posted to you or collected from the union) are printed with “Your Name”, and “Guest of Your
Name”, eliminating the risk of touting (assuming that reasonable checks are made by security at the gate – just checking the identity of every fifth person in would act as sufficient
deterrent to those who would like to go to the ball using a ticket in somebody else’s name).
The e-mail confirmation also gives people a chance to change their mind: if their friends, who they wanted to go with, were unable to get tickets before they all sold out, for example,
they would know about it and be able to cancel their order. But it would also ensure the identity of the purchaser without requiring them to pass their password over the network.
Students collecting tickets from the union would have to produce photo ID.
Those tickets remaining unsold after the web server is hammered by requests for tickets (for example, those cancelled or released later) would all be sold in a “second wave” (which
would be announced in advance).
It is terribly unfair for the union to make students stand out in the cold and the rain, without sleep, to get tickets to an event; it could even be argued as discriminatory (whereas
the University ensures that all students have the capacity and tools to use an internet connection). There would be no queues, no touts, and no unfairness. There would be no fights for
the limited amount of cash in the on-campus cashpoints. The union would save money in ticket salespeople and policing the queue. And a system like this could be implemented for them for
a sum of money that could be measured in the hundreds, not the thousands, of pounds. Hell; I will quote them for it, if they ask: I’ve already knocked up a prototype.
Why not send a message to the May Ball organisers and tell them what a good idea it would be,
particularly if it would make the difference to you, personally, about going to the May Ball.
They still won’t listen.