This telegraph pole in the centre of Eynsham carries the scars of hosting countless community announcements, notices, and flyers over the last 30 years.
Tag: telephone
Note #27434
Somebody just called me and quickly decided it was a wrong number. The signal was bad and I wasn’t sure I’d heard them right, so I followed up by replying by text.
It turns out they asked Siri to call Three (the mobile network). Siri then presumably searched online, found Three Rings, managed to connect that to my mobile number, and called me.
If Siri’s decided that I represent Three, this could work out even worse than that time Google shared my phone number.
Google Shared My Phone Number!
Podcast Version
This post is also available as a podcast. Listen here, download for later, or subscribe wherever you consume podcasts.
Earlier this month, I received a phone call from a user of Three Rings, the volunteer/rota management software system I founded1.
We don’t strictly offer telephone-based tech support – our distributed team of volunteers doesn’t keep any particular “core hours” so we can’t say who’s available at any given time – but instead we answer email/Web based queries pretty promptly at any time of the day or week.
But because I’ve called-back enough users over the years, it’s pretty much inevitable that a few probably have my personal mobile number saved. And because I’ve been applying for a couple of interesting-looking new roles, I’m in the habit of answering my phone even if it’s a number I don’t recognise.

After the first three such calls this month, I was really starting to wonder what had changed. Had we accidentally published my phone number, somewhere? So when the fourth tech support call came through, today (which began with a confusing exchange when I didn’t recognise the name of the caller’s charity, and he didn’t get my name right, and I initially figured it must be a wrong number), I had to ask: where did you find this number?
“When I Google ‘Three Rings login’, it’s right there!” he said.
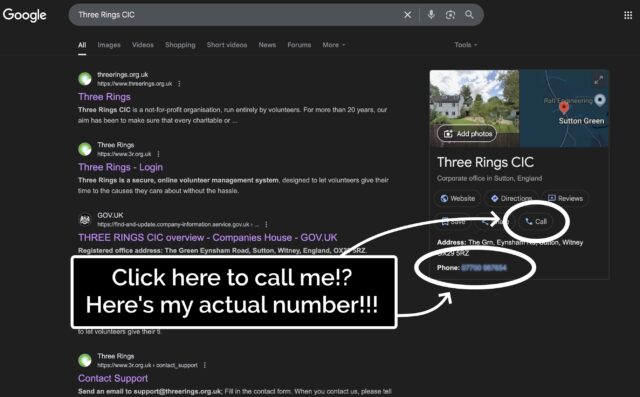
He was right. A Google search that surfaced Three Rings CIC’s “Google Business Profile” now featured… my personal mobile number. And a convenient “Call” button that connects you directly to it.
Some years ago, I provided my phone number to Google as part of an identity verification process, but didn’t consent to it being shared publicly. And, indeed, they didn’t share it publicly, until – seemingly at random – they started doing so, presumably within the last few weeks.
Concerned by this change, I logged into Google Business Profile to see if I could edit it back.
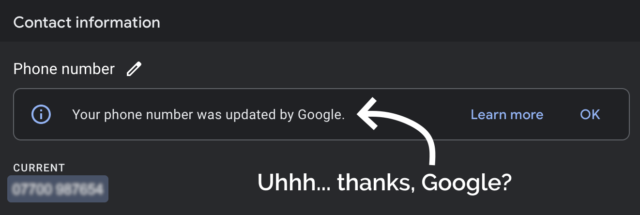
I deleted my phone number from the business listing again, and within a few minutes it seemed to have stopped being served to random strangers on the Internet. Unfortunately deleting the phone number also made the “Your phone number was updated by Google” message disappear, so I never got to click the “Learn more” link to maybe get a clue as to how and why this change happened.
Last month, high-street bank Halifax posted the details of a credit agreement I have with them to two people who aren’t me. Twice in two months seems suspicious. Did I accidentally click the wrong button on a popup and now I’ve consented to all my PII getting leaked everywhere?
Such feelings of rage.
Footnotes
1 Way back in 2002! We’re very nearly at the point where the Three Rings system is older than the youngest member of the Three Rings team. Speaking of which, we’re seeking volunteers to help expand our support team: if you’ve got experience of using Three Rings and an hour or two a week to spare helping to make volunteering easier for hundreds of thousands of people around the world, you should look us up!
2 Seriously: if you’re still using Google Search as your primary search engine, it’s past time you shopped around. There are great alternatives that do a better job on your choice of one or more of the metrics that might matter to you: better privacy, fewer ads (or more-relevant ads, if you want), less AI slop, etc.
Rosgill Crossroads
I’m in an extremely rural area and I needed a phone call with my lawyer about my recent redundancy. Phone signal was very bad, so I resolved to climb a nearby hill and call him back.
“I’m at a crossroads,” I said, when I finally found enough bars to have a conversation with him.
“In your life?” he asked.
“I guess,” I replied, “But also, y’know, literally.”
Yr Wyddfa’s First Email
On Wednesday, Vodafone announced that they’d made the first ever satellite video call from a stock mobile phone in an area with no terrestrial signal. They used a mountain in Wales for their experiment.
It reminded me of an experiment of my own, way back in around 1999, which I probably should have made a bigger deal of. I believe that I was the first person to ever send an email from the top of Yr Wyddfa/Snowdon.
Nowadays, that’s an easy thing to do. You pull your phone out and send it. But back then, I needed to use a Psion 5mx palmtop, communicating over an infared link using a custom driver (if you ever wondered why I know my AT-commands by heart… well, this isn’t exactly why, but it’s a better story than the truth) to a Nokia 7110 (fortunately it was cloudy enough to not interfere with the 9,600 baud IrDA connection while I positioned the devices atop the trig point), which engaged a GSM 2G connection, over which I was able to send an email to myself, cc:’d to a few friends.
It’s not an exciting story. It’s not even much of a claim to fame. But there you have it: I was (probably) the first person to send an email from the summit of Yr Wyddfa. (If you beat me to it, let me know!)
The Right Prop
Sometimes you just gotta have exactly the right prop for a presentation…
Transferring to a new phone network, 2022 edition
This is a repost promoting content originally published elsewhere. See more things Dan's reposted.
…removing a SIM tray is harder than it looks when you don’t wear earrings. I had to search everywhere to find one of those little SIM tools…
Stuart writes a fun article about his experience of changing mobile network. It’s worth a read, and there’s only one “Dan pro tip” I’d add:
If you have a case on your mobile phone, tuck one of those SIM extractor tools into the case, behind your phone. It’s exactly where you need it to be, if you need one yourself (you probably need to remove the case to access the SIM tray anyway), but beyond that: it means you’re always carrying one for when a friend needs one. They’re also useful for pressing those tiny “factory reset” buttons you see sometimes.
A SIM extractor has been sneakily part of my “everyday carry” for about a decade and it’s proven its value time and time again.
Note #20645
Unable to sleep, I found myself wondering whether anybody with a retro-hipster vibe had built a smart pocketwatch. All your smartwatch features, but in pocketwatch format.
Then I realised I was describing a mobile phone on a keychain.
Note #19590
Review of Vodafone
This review of Vodafone originally appeared on Google Maps. See more reviews by Dan.
Like most mobile phone shops, this one enjoys a confusing layout and less-than-completely-helpful staff.
If you know exactly what you want then you can have a reasonable experience, but if you know exactly what you want then you’d be better to go online. If you’re not sure what you want, you’re going to have an unhappy time full of upselling and jargon… so you’d do better to go online.
The network itself is good: broad coverage, good data speeds, nice international deals. But this shop is a perfect example of why their shops ought to already be a relic of history.
Looking for red phone boxes in Oxford. Can you help?
This self-post was originally posted to /r/oxford. See more things from Dan's Reddit account.
I’m trying to index the location of red telephone boxes in Oxford, for a project I’m doing. I’m especially interested in ones outside of the city centre (it’s easy to find the ones on Broad Street, High Street, Parks Road, St. Giles, etc.). If you’re aware of any, or if you’re e.g. willing to keep your eyes open for them on the way to and from work/class/wherever for the next couple of days, I’d really appreciate it. Also happy to throw Reddit Gold at people who are particularly helpful.
Want me to send you a reminder in a few days, once you’ve been looking for them? Leave a comment, and I’ll PM you a few days later. Want to know what the project is? Find a box for me that I haven’t got on my list, and I’m happy to PM you the details.
Thanks!
Pocket Searching
Pocket dialling was bad enough. I once received a phone call from a friend whose phone called me – as the last number he’d dialled – just as he was putting on a harness in anticipation of doing a bungee jump. So all I got to hear was rustling, and shuffling… and then a blood-curdling scream. Nice one.

But in this age of smartphones, the pocket search has become a new threat. Thanks to the combination of touchscreens, anticipatory keyboards (I use SwiftKey, and I’m beginning to think that it knows me better than I do myself), and always-online devices, we’re able to perform quite complex queries quite accidentally. I’ve got a particular pair of trousers which seems to be especially good at unlocking my phone, popping up a search engine, typing a query (thanks to the anticipatory keyboard, usually in full words), and then taking a screenshot and saving it for me, so that I can’t later deny having searched for… whatever it was.
This morning, while cycling to work, I searched for the following (which I’ve reformatted by inserting line breaks, in order to transform it into the sort-of poem you might expect from sombebody both insane and on hallucinogens):
thanks again
and it all goes on
and I will Also
Also A bit LIKE THAT
THE ANSWER is
That you are looking at your Local Ryanair
and a ripening
and a ripening
I can assure are a BIT
and see the new template by clicking here
for
for YOU GUYS
GUYS HAVE YOU ANY COMMENTS
ON MY WAY BACK FROM YOU
And the other side and I will have the same
as a friend or relative
relative humidity
humidity
to you
you are here car
car
and
and embarrassing
embarrassing
the best thing is the first three years and over
over?
Maybe my phone is gradually becoming sentient and is trying to communicate with me. I for one welcome our new robot overlords.
Phone Security == Computer Security
The explosion of smartphone ownership over the last decade has put powerful multi-function computers into the pockets of almost half of us. But despite the fact that the average smartphone contains at least as much personally-identifiable information as its owner keeps on their home computer (or in dead-tree form) at their house – and is significantly more-prone to opportunistic theft – many users put significantly less effort into protecting their mobile’s data than they do the data they keep at home.

I have friends who religiously protect their laptops and pendrives with TrueCrypt, axCrypt, or similar, but still carry around an unencrypted mobile phone. What we’re talking about here is a device that contains all of the contact details for you and everybody you know, as well as potentially copies of all of your emails and text messages, call histories, magic cookies for social networks and other services, saved passwords, your browsing history (some people would say that’s the most-incriminating thing on their phone!), authentication apps, photos, videos… more than enough information for an attacker to pursue a highly-targeted identity theft or phishing attack.

“Pattern lock” is popular because it’s fast and convenient. It might be good enough to stop your kids from using your phone without your permission (unless they’re smart enough to do some reverse smudge engineering: looking for the smear-marks made by your fingers as you unlock the device; and let’s face it, they probably are), but it doesn’t stand up to much more than that. Furthermore, gesture unlock solutions dramatically reduce the number of permutations, because you can’t repeat a digit: so much so, that you can easily perform a rainbow table attack on the SHA1 hash to reverse-engineer somebody’s gesture. Even if Android applied a per-device psuedorandom salt to the gesture pattern (they don’t, so you can download a prefab table), it doesn’t take long to generate an SHA1 lookup of just 895,824 codes (maybe Android should have listened to Coda Hale’s advice and used BCrypt, or else something better still).

These attacks, though (and the iPhone isn’t bulletproof, either), are all rather academic, because they are trumped by the universal rule that once an attacker has physical access to your device, it is compromised. This is fundamentally the way in which mobile security should be considered to be equivalent to computer security. All of the characteristics distinct to mobile devices (portability, ubiquity, processing power, etc.) are weaknesses, and that’s why smartphones deserve at least as much protection as desktop computers protecting the same data. Mobile-specific features like “remote wipe” are worth having, but can’t be relied upon alone – a wily attacker could easily keep your phone in a lead box or otherwise disable its connectivity features until it’s cracked.

The only answer is to encrypt your device (with a good password). Having to tap in a PIN or password may be less-convenient than just “swipe to unlock”, but it gives you a system that will resist even the most-thorough efforts to break it, given physical access (last year’s iPhone 4 vulnerability notwithstanding).
It’s still not perfect – especially here in the UK, where the RIPA can be used (and has been used) to force key surrender. What we really need is meaningful, usable “whole system” mobile encryption with plausible deniability. But so long as you’re only afraid of identity thieves and phishing scammers, and not being forced to give up your password by law or under duress, then it’s “good enough”.
Of course, it’s only any use if it’s enabled before your phone gets stolen! Like backups, security is one of those things that everybody should make a habit of thinking about. Go encrypt your smartphone; it’s remarkably easy –
- Android
- iPhone – just enable PIN lock, but consider also encrypting your backups
- BlackBerry
- Windows Phone – encryption is “coming soon”, apparently.
Searching For A Virgin
You just can’t rely on GMail’s “contacts” search any more. Look what it came up with:

With apologies to those of you who won’t “get” this: the person who came up in the search results is a name that is far, far away, in my mind, from the word “virgin”.
In not-completely-unrelated news, I use a program called SwiftKey X on my phone, which uses Markov chains (as I’ve described before) to intelligently suggest word completion and entire words and phrases based on the language I naturally use. I had the software thoroughly parse my text messages, emails, and even this blog to help it learn my language patterns. And recently, while writing a text message to my housemate Paul, it suggested the following sentence as the content of my message:
I am a beautiful person.
I have no idea where it got the idea that that’s something I’m liable to say with any regularity. Except now that it’s appeared on my blog, it will. It’s all gone a little recursive.
What’s Wrong With My Phone
In my review of my new HTC Sensation earlier this month, I tried to explain how my new phone – with it’s swish and simple interface – didn’t feel quite… geeky enough for me. I picked up on the way that it’s process management works, but I’ve since realised that this is only symptomatic of a deeper problem. This is entirely to do with the difference between traditional computers (of which my old N900 was one) and modern consumer-centric devices (which, inspired by the iPod/iPhone/iPad/etc.) try to simplify things for the end-user and provide strong support for centralised repositories of pre-packaged “apps” for every conceivable purpose.

To take an example of the difference: my N900 ran Linux, and felt like it ran Linux. As a reasonably-sensible operating system, this meant that all of the applications on it used pretty much the same low-level interfaces to do things. If I wanted, I could have installed (okay, okay – compiled) sshfs, and be reasonably confident that every application on my phone, whether it’s a media player or a geocaching application or whatever, would use that new filesystem. I could store my geocaching .gpx files on an SSH-accessible server somewhere, and my phone could access them, and my geocaching app wouldn’t know the difference because I’d have that level of control over the filesystem abstraction layer.
Similarly, if I installed a game which made use of Ogg Vorbis to store its sound files, which therefore installed the Vorbis codecs, then I can expect that my media player software will also be able to make use of those codecs, because they’ll be installed in the standard codec store. This kind of thing “just works”. Okay, okay: you know as well as I do that computers don’t always “just work”, but the principle is there such that it can “just work”, even if it doesn’t always.
On these contemporary smartphones, like the iPhone, Android devices, and (I assume) modern BlackBerrys, the model is different: individual applications are sandboxed and packaged up into neat little bundles with no dependencies outside of that provided by the platform. If you have two applications installed that both use sshfs, then they both have to include (or implement) the relevant bundle! And having them installed doesn’t automatically give sshfs-like functionality to your other filesystem-accessing tools.
It’s not all bad, of course: this “new model” is great for helping non-technical users keep their devices secure, for example, and it means that there’s almost no risk of dependency hell. It’s very… easy. But I’m still not sure it quite works: I’ll bet that 90% of users would install an application that demands dubious levels of permissions (and could, for example, be stealing their address book data for sale to scammers) without even thinking about the risks, so the security benefits are somewhat nullified.
In summary:
| Pros | Cons | |
|---|---|---|
| Traditional-computing device (e.g. N900) |
|
|
| “New model” device (e.g. iPhone, Android) |
|
|
Needless to say, the new model devices are winning, and already tablet computers powered by the very same platforms as the mobile phones are beginning to be seen as a simpler, easier alternative to conventional laptops. It’s to be expected: most of today’s users don’t want a learning curve before they can use their smartphone: they just want to make some calls, play Angry Birds a bit, keep up with their Facebook friends, and so on. But I hope that there’ll always be room for a few folks like me: folks who want to tinker, want to play, want to hack code for no really benefit but their own pleasure… and without having to shell out for a developer license in order to do so!


