I’m staying in a lodge in the Yorkshire Dales National Park to celebrate the eldest kid’s birthday and we’ve just received a huge dump of snow, overnight. What was grass is now a thick white carpet of fresh powder. Sounds like a great birthday present for an excited kid I can just hear beginning to wake up…
Author: Dan Q
Dan Q did not find GC8TK41 05 – Willow’s Wanders – Eshington Bridge
This checkin to GC8TK41 05 - Willow's Wanders - Eshington Bridge reflects a geocaching.com log entry. See more of Dan's cache logs.
An extended search over two visits today by the eldest child and I couldn’t reveal this one. Very frustrating, given that it’s clearly there somewhere (CO performed maintenance just yesterday!). We’re staying in a cabin a little way downstream, so we might find another opportunity to search again tomorrow, weather-permitting. 🤞
Dan Q found GC80592 Coffee, Cache and Dash
This checkin to GC80592 Coffee, Cache and Dash reflects a geocaching.com log entry. See more of Dan's cache logs.
QEF while stopped for a confort break on a long journey North from Oxford. The dog wanted to go with the others into the services, but had to stay outdoors with me and hunt for the cache. Solid hint!

My Ball
Our beloved-but-slightly-thick dog will sometimes consent to playing fetch, but one of her favourite games to play is My Ball. Which is a bit like fetch, except that she won’t let go of the ball.
It’s not quite the same as tug-of-war, though. She doesn’t want you to pull the toy in a back-and-forth before, most-likely, giving up and letting her win1. Nor is My Ball a solo game: she’s not interested in sitting and simply chewing the ball, like some dogs do.

No, this is absolutely a participatory game. She’ll sit and whine for your attention to get you to come to another room. Or she’ll bring the toy in question (it doesn’t have to be a ball) and place it gently on your foot to get your attention.
Your role in this game is to want the ball. So long as you’re showing that you want the ball – occasionally reaching down to take it only for her to snatch it away at the last second, verbally asking if you can have it, or just looking enviously in its general direction – you’re playing your part in the game. Your presence and participation is essential, even as your role is entirely ceremonial.

Playing it, I find myself reminded of playing with the kids when they were toddlers. The eldest in particular enjoyed spending countless hours playing make-believe games in which the roles were tightly-scripted2. She’d tell me that, say, I was a talking badger or a grumpy dragon or an injured patient but immediately shoot down any effort to role-play my assigned character, telling me that I was “doing it wrong” if I didn’t act in exactly the unspoken way that she imagined my character ought to behave.
But the important thing to her was that I embodied the motivation that she assigned me. That I wanted the rabbits to stop digging too near to my burrow3 or the princess to stay in her cage4 or to lie down in my hospital bed and await the doctor’s eventual arrival5. Sometimes I didn’t need to do much, so long as I showed how I felt in the role I’d been assigned.

Somebody with much more acting experience and/or a deeper academic comprehension of the performing arts is going to appear in the comments and tell me why this is, probably.
But I guess what I mean to say is that playing with my dog sometimes reminds me of playing with a toddler. Which, just sometimes, I miss.
Footnotes
1 Alternatively, tug-of-war can see the human “win” and then throw the toy, leading to a game of fetch after all.
2 These games were, admittedly, much more-fun than the time she had me re-enact my father’s death with her.
3 “Grr, those pesky rabbits are stopping me sleeping.”
4 “I’ll just contentedly sit on my pile of treasure, I guess?”
5 Playing at being an injured patient was perhaps one of my favourite roles, especially after a night in which the little tyke had woken me a dozen times and yet still had some kind of tiny-human morning-zoomies. On at least one such occasion I’m pretty sure I actually fell asleep while the “doctor” finished her rounds of all the soft toys whose triage apparently put them ahead of me in the pecking order. Similarly, I always loved it when the kids’ games included a “naptime” component.
Note #25428
Frogs in a Hollow pt 2
This evening I used leftover cocktail sausages to make teeny-tiny toads-in-the-hole (my kids say they should be called frogs-in-the-dip).
It worked out pretty well.
Micro-recipe:
1. Bake cocktail sausages (or veggie sausages, pictured) until barely done.
2. Meanwhile, make a batter (per every 6 sausages: use 50ml milk, 50g plain flour, 1 egg, pinch of salt).
3. Remove sausages from oven, then turn up to 220C.
4. Put a teaspoon of a high-temperature oil (e.g. vegetable, sunflower) into each pit of a cake/muffin tin, return to oven until almost at smoke point.
5. Add a sausage or two to each pit and return to the oven for a couple of minutes to come back up to temperature.
6. Add batter to each pit. It ought to sizzle when it hits the oil, if it’s hot enough. Return to the oven.
7. Remove when puffed-up and crisp. Serve with gravy and your favourite comfort food accompaniments.
Frogs in a Hollow pt 1
Trifle for Breakfast
Note #25419
Book Exchange
Our family Christmas Eve tradition, which we absolutely stole from Icelandic traditions (cultural appropriation? I’m not sure…) via some newspaper article we saw years ago, is a book exchange.
verybody gives each other person a book,then we sit around and read until people retire to bed (first the kids, then – eventually – the adults).
We love it.
Note #25413
Xmas Post
Note #25406
Too Late
Moving Three Rings’ Servers
Yesterday, I fulfilled the primary Three Rings objective I set for myself when I kicked off my sabbatical twelve weeks ago and migrated the entire application to a new hosting provider (making a stack of related improvements along the way).
I did some work on this project during my Three Rings-focussed International Volunteer Day last week, but it feels like I’ve been working on it for much longer than that. And it feels like it… because I have been.
Months prior, I was comparing different providers and their relative merits, making sure that our (quirky and specific) needs could be met. Weeks beforehand, I was running a “dry run” every four or five days, streamlining the process of moving the ~450GB1 of live data while minimising downtime. Days before the event felt like the countdown for a rocket launch, with final preparations underway: reducing DNS time-to-lives, ensuring users knew about our downtime window, and generally fitting in a little time to panic.
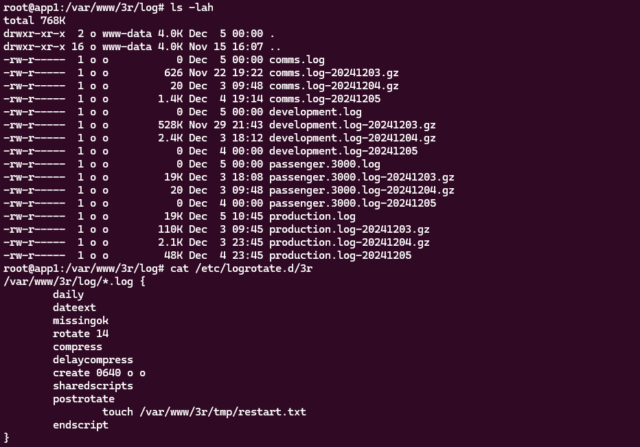
logrotate. When you’re building architecture for a system as gnarly as Three Rings, there’s
about a billion tools that need such careful tweaking2.
It’s challenging to pull off a “big”, intensive operation like this in an entirely voluntary operation. I’m not saying I couldn’t have done it were I not on sabbatical, but it’d certainly have been harder and riskier.
But then, I also couldn’t have done it without the kickass team of volunteers I’ve surrounded myself with. I guess the real success story here is in the power of a well-aligned team and in volunteer effort.
Footnotes
1 Three Rings‘ user data is represented by a little under 70GB of MariaDB databases plus about 380GB of organisational storage: volunteer photos, files, email attachments, and the like. Certainly not massive by comparison to, say, social media sites, search engines, and larger eCommerce platforms… but large enough that moving it takes a little planning!
2 Okay, a billion tools to configure? That’s an exaggeration. Especially now: since the architectural changes I’ve put in place this week, for example, production app server builds of Three Rings no require a custom-compiled build of Nginx (yes, this really was something we used to need).
3 Which you’d think I’d have realised with my more-successful recent second attempt at secret-cabinet-making.










