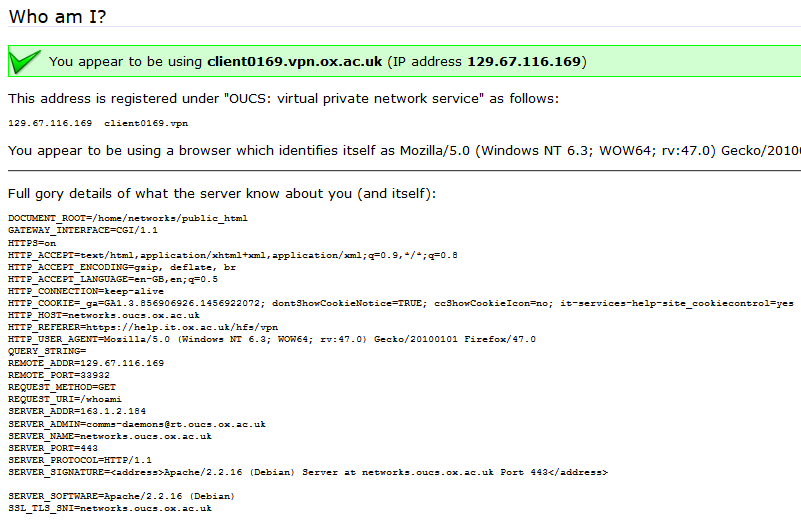
At a little over 590 thousand words and spanning 1,349 pages, Vikram Seth’s A Suitable Boy is almost-certainly among the top ten longest single-volume English-language novels. It’s pretty fucking huge.

I only discovered A Suitable Boy this week (and haven’t read it – although there are some good reviews that give me an inclination to) when, on a whim, I decided to try to get a scale of how much I’d ever written on this blog and then decided I needed something tangible to use as a comparison. Because – give or take – that’s how much I’ve written here, too:
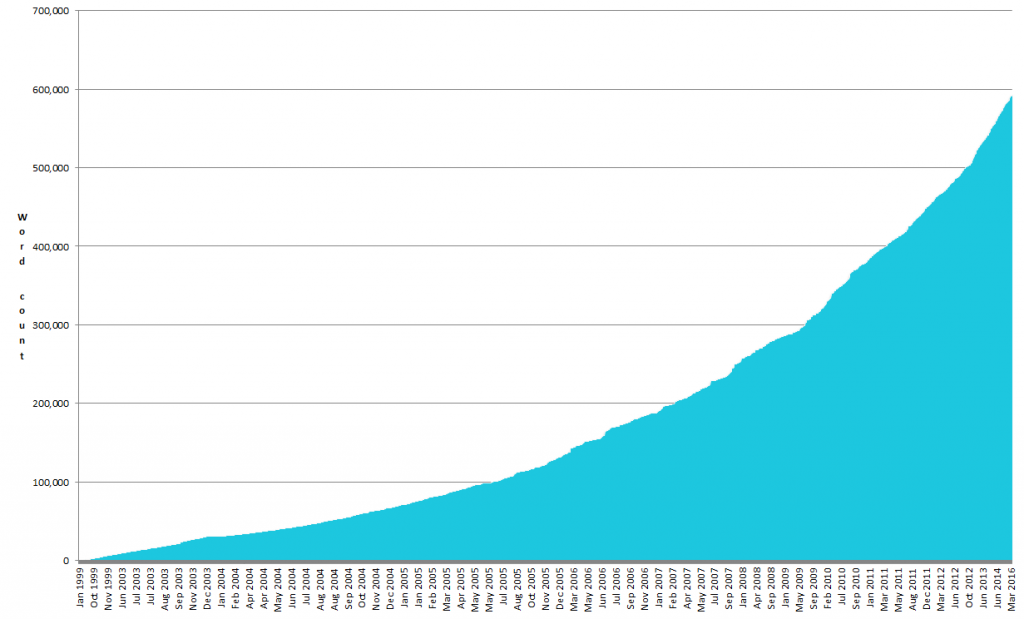
Of course, there’s some caveats that might make you feel that the total count should be lower:
- It might include a few pieces of non-content code, here and there. I tried to strip them out for the calculation, but I wasn’t entirely successful.
- It included some things which might be considered metadata, like image alt-text (on the other hand, sometimes I like to hide fun messages in my image alt-text, so perhaps they should be considered content).
On the other hand, there are a few reasons that it perhaps ought to be higher:
- It doesn’t include any of the content “lost” during the July 2004 server failure, some of which (like this post about Orange) were later recovered but many of which (like this post about Christmas plans and upcoming exams) remain damaged. It also doesn’t include any of the lost content from the original 1998/1999 version of this blog, only the weird angsty-teen out-of-context surviving bits.
- Post titles (which sometimes contain part of the content) and pages outside of blog posts are not included in the word count.
- I’ve removed all pictures for the purpose of the word count. Tempting though it was to make each worth a thousand words, that’d amount to about another one and a half million words, which seemed a little excessive.

Of course, my blog doesn’t really have a plot like A Suitable Boy (might compare well to the even wordier Atlas Shrugged, though…): it’s a mixture of mostly autobiographical wittering interspersed with musings on technology and geekery and board games and magic and VR and stuff. I’m pretty sure that if I knew where my life would be now, 18 years ago (which is approximately when I first started blogging), I’d have, y’know, tried to tie it all together with an overarching theme and some character development or something.
Or perhaps throw in the odd plot twist or surprise: something with some drama to keep the reader occupied, rather than just using the web as a stream-of-conciousness diary of whatever it is I’m thinking about that week. I could mention, for example, that there’ll be another addition to our house later this year. You heard it here first (unless you already heard it from somewhere else first, in which case you heard it there first.)

Still: by the end of this post I’ll have hit a nice, easy-to-remember 594,000 words.