In the field of software development, there’s always something new to learn. Whether it’s a new language, framework, API or methodology, your need to study is never through –
even if you’re a FORTRAN developer. But one of the more
esoteric areas of your education will come in the form of the language programmers use, and I don’t mean programming languages.
And so I present to you a dictionary of modern programmer language (much of it shamelessly lifted from a discussion on Stack Overflow):
Ajah
Ajax, but returning HTML rather than XML (e.g. using jQuery‘s $.load method). Similarly, Ajaj, when you expect script to be
returned (e.g. $.getScript).
Bicrement
Adding 2 to a number.
Boolean Zen
A principle of programming lacked by those who perform expressions to compare variables to boolean constants. For example, if (userHasLoggedIn == true) lacks Boolean Zen,
because the == true at best does nothing at all, and at worst results in an unnecessary evaluation.
Classtrophobia
When someone chooses not to use the obvious object-oriented approach when it is available.
Common Law Feature
A bug in some software which has existed so long that it has begun to be depended upon by the users, who will complain loudly when it is “fixed”.
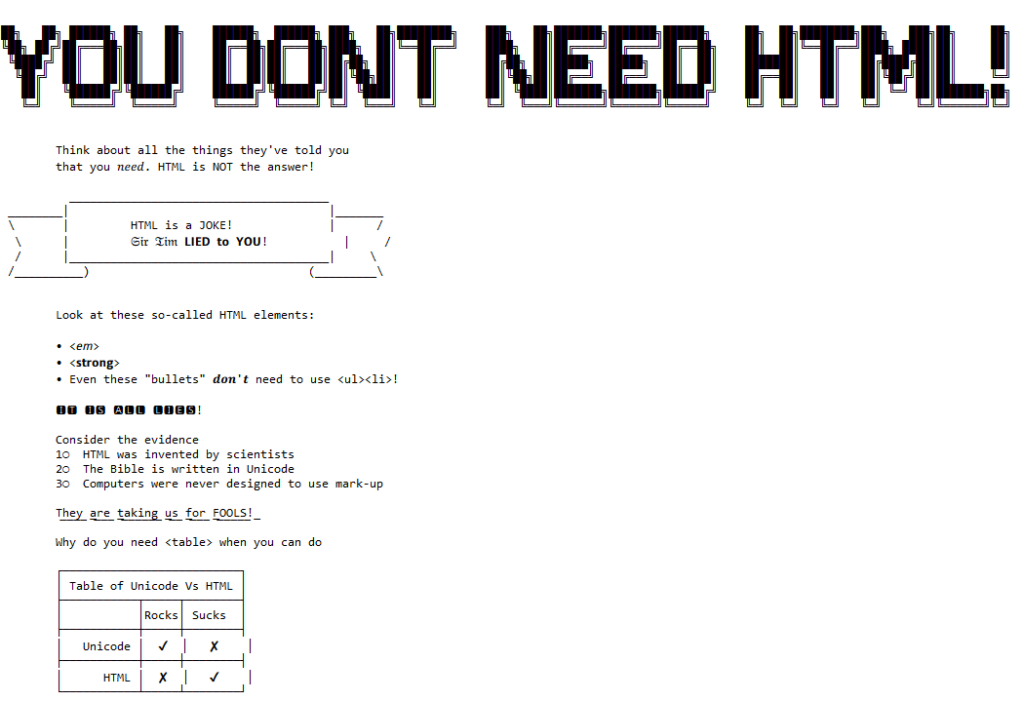
Doctype Decoration
In web development, the practice of putting a Doctype Declaration (e.g. <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.1//EN"
"http://www.w3.org/TR/xhtml11/DTD/xhtml11.dtd">) into the document despite not actually writing standards-compliant code. Often accompanied by putting a “Valid HTML & CSS”
link on the site, but never actually checking that the site passes the validator’s test.
Egyptian Brackets
That style of coding which puts the opening brace { of a block on the same line as the expression (wrapped in parentheses) before it, e.g.:
if (expression){
So called because the ){ sort-of looks like a stereotypical ancient Egyptian pose, depending on your preferred coding font:

Floater
A bug that sits at the top of the bug tracking system, but nobody claims responsibility for it. Everybody just works around it.
Flock of Geese Code
A block of deeply-nested and heavily-indented code forming a tight V-shaped wedge. Often occurs when adding functionality to a complex block of evaluations, by a developer who hasn’t
noticed that perhaps a return statement, exception-handling, the && operator or even a goto statement might be more appropriate! Especially
poignant when using a bracketed-block language, where you’ll see a string of closing braces flying away at the end of the code.
Hi-Driven Development
A variety of printf-debugging where you pepper your code with alert('hi'); in order to find out where it’s going wrong, rather than breaking out a proper debugger. Other
acceptable string literals include “hello”, “here”, “xyzzy”, etc.
Higgs-Bugson
A bug that you believe to exist based on sparse log data and theoretical examination, but you have no evidence to support the idea that it has ever actually been observed, except
perhaps vague anecdotal evidence from users.
Hindenbug
A catastrophic bug resulting in a devastating loss (typically of data). “Oh, the humanity!”
headlessCamels
CamelCase words lacking a leading capital letter, as required or recommended for various languages, frameworks, and styles. As opposed to ProudCamels.
Heisenbug
First noticed on Usenet in the 80s, but still awesome: a bug that defies investigation because, during debugging (when you’re observing it), it behaves differently.
Hydra Code
Code so bug-riddled that killing one problem results in two more in it’s place, like the mythological Lernaean Hydra‘s many
heads.
IRQed
Interrupted while you were trying to program. Not necessarily by somebody with an actual flag.
Loch Ness Monster Bug
An important bug, if ever it could be proven to exist. Only ever observed once or twice by users who were unable to back up or reproduce their claims. These users often go on to swear
by the existence of the bug, blaming it for all kinds of unusual phenomena even in completely unrelated systems for years to come.
Ninja Comments
Comments which are so stealthy that you can’t see them at all. It’s almost as if the code weren’t documented at all!
NOPping
Like napping, but what programmers do while they’re downtiming while waiting for a computer to finish a task. Based on the NOOP or NOP operation found in many low-level languages.
NP Hilarious
An algorithm whose complexity is a joke, whether deliberately (e.g. Bogosort, but not Quantum Bogosort) or not.
Object Oriented Pasta
Spaghetti code wrapped up into classes to look like proper object-oriented code. Also Ravioli.
Pokémon Exception Handling
For when you positively, absolutely, “gotta catch ’em all.” I’m talking about hideous code like this:
try {
MessageBox.Show(message);
} catch(Exception exc) {
MessageBox.Show(exc.Message);
}
See also Try, Catch, Forget.
Refucktoring
As defined by Jason Gorman: refactoring code in such a way that you are now the only person capable of maintaining it. E.g.
stripping all comments and whitespace from an arcane bit of code that you wrote in order to give yourself the illusion of being indispensable. Results in Mortgage Code (code
which pays your mortgage because you can’t be fired while it exists).
Rubberducking
Sometimes you’re working on a problem and what you really need to do to solve it is to talk through the problem with somebody else. The other person doesn’t even need to be a developer:
often, they don’t even need to listen – they just need to be there while you talk your way to your own solution. So much so, that they might as well be replaced with a rubber
duck, sat atop your monitor. A name come up with by a programmer who apparently actually did this.
Scar Tissue
Commented-out blocks of old code, after refactoring, that have been checked in to the main codebase.
Shrug Report
A bug report which contains no reproducible information whatsoever, or is so unclear as to be ambiguous. Often contains phrases like “doesn’t work”, or doesn’t show how the anticipated
behaviour differs from that observed (e.g. “when I click the print icon, the document is printed onto A4 paper from the feeder tray of the printer”).
Smug Report
A bug report submitted by a user who acts as if they know more about the system than the developer does.
Stringly-Typed
Use of strings for all kinds of inappropriate variables, like strings containing the words “true” and “false” for use in comparisons (not helped by the fact that some languages, like
PHP, will let you get away with boolean comparisons on these). Also common among inexperience database developers, who’ll make an entire database of
VARCHARs because they’re then able to store whatever they want in there, right?
Troolian Logic
Using a boolean variable to deliberately hold three states of information: true, false, and null. Often requires the use of the === operator to function properly.
Try, Catch, Forget
An exception handling strategy based purely on catching exceptions and then doing nothing with them. In other words, telling your program “if something goes wrong… carry on anyway!”
Sometimes also seen as a Trynally – a block of code with a try and a finally block, but no catch blog at all. See also Pokémon
Exception Handling.
Unicorny
Adjective used to describe a requested feature that’s so early in the planning stages it might as well be imaginary. Used by Yehuda Katz to describe some of Rails‘ upcoming features.
Yoda Conditions
Expressions that test for (literal == variable) rather than the more-common (variable == literal). The former is preferred by some programmers because it
reduces the risk of accidentally using a single-equals rather than a double-equals (this mistake would produce a compiler error rather than simply misbehaving). So-called because it
results in Yoda-like phraseology (e.g. “has no errors, the form does”).