This checkin to GC23WKZ Alpha reflects a geocaching.com log entry. See more of Dan's cache logs.
Yet another failed-to-find. =o(
This checkin to GC23WKZ Alpha reflects a geocaching.com log entry. See more of Dan's cache logs.
Yet another failed-to-find. =o(
This checkin to GC1J9XJ Middlewood Circular - Bridge 34 reflects a geocaching.com log entry. See more of Dan's cache logs.
Log is soaked; unusable – needs replacement.
This checkin to GL3DFKZC BVW #1 reflects a geocaching.com log entry. See more of Dan's cache logs.
Great little cache in a lovely area; quite a bit out of our way, but wanted some first-time cachers amongst us to see a non-micro cache (we’d previously been getting a few along the canal). Signed the log, left a toy robot, took nothing (cache contents were kinda sparse, so thought it needed a little extra in it). TFTH.
This checkin to GL3DFKWG Middlewood Circular - Bridge 33 reflects a geocaching.com log entry. See more of Dan's cache logs.
Almost didn’t find this – looked in all of the obvious hiding places several times before we actually looked in the right one (hampered a little by the morning’s snowfall)! Log damp, but usable. TFTC.
This checkin to GL3DFKRK Macclesfield Canal - Bridge 35 reflects a geocaching.com log entry. See more of Dan's cache logs.
Great hiding place! TFTC.
This checkin to GL3DFKPE Middlewood Circular - Bridge 34 reflects a geocaching.com log entry. See more of Dan's cache logs.
Took some friends, local to the area, out for their first caching expedition: this was our first find of the day. One of the new ‘uns was the first to spot where this little cache was hidden. Log completely soaked – added a little more paper from a scrapbook but this is only a short-term fix: needs some fresh rolls.
Today, I had to explain to somebody that Mozilla Firefox is free*.
Let me elaborate slightly. Today, I had to explain to an IT professional that Mozilla Firefox is free.
Let me go a tiny bit further. Today, I had to explain to an IT professional with decades of experience, working for an very large government-funded body, that Mozilla Firefox is free. This isn’t some kid who got started on Windows XP. This is a man who remembers the first browser war. A man who works on UNIX systems in his day-to-day work, I gather. A man who should know better. Surely! Surely?
This is where your tax money is going. I think the UK FOSS advocacy scene just died a little inside.
* Free as in beer, for those that are counting.
A few months ago, I spent one lunchtime writing a One-Time Pad Encryption/Decryption Engine in Javascript. I’d meant to blog about it at the time, but I forgot, but I came across it again today and thought it was cool enough to share with you all.
If you already appreciate why that’s cool, go play with it. If you don’t, allow me to explain.
What is a One-Time Pad and why is it awesome?
One-time pads are a form of cryptography which are simple enough to do by hand (you don’t need a computer, but it helps), versatile enough to transport any message, and – this is the clever part – completely unbreakable.
Yes, completely unbreakable. It doesn’t matter if you have a billion supercomputers and a billion years, a one-time pad is mathematically sound. So long as it’s used properly, it’s unbreakable, but it’s the difficulty and discipline required in using them properly – as well as difficulties in finding secure ways to share keys over long distances – that makes them impractical for widespread use.
They did, however, see a lot of use in espionage during the Second World War and the Cold War, and continue to be used today for some diplomatic messages, as well as occasionally by particularly paranoid civilians.
So what’s the story?
You’re probably familiar with the concept of a Caesar Cipher – you may have even played with them as a child – which is perhaps most-often seen nowadays in the form of ROT13. Put simply, a caesar cipher “rotates” letters through the alphabet, so perhaps A becomes B, B becomes C, C becomes D, and so on (in this example, Z would become A). So my message “IF YOU READ THIS YOU ARE GAY” becomes “JG ZPV SFBE UIJT ZPV BSF HBZ”. I can send that message to you, having already agreed with you the code, and you can roll each letter back by one (so A becomes Z, B becomes A, etc.), to get back the original message.
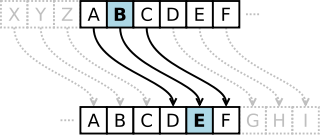
This is fundamentally flawed and offer no real security at all, of course. But suppose we made a couple of enhancements to our plain old Caesar Cipher. First, let’s add some punctuation to our alphabet (space, full stop, comma – we’ll treat these as letters in their own right which come after ‘Z’). Then, instead of rotating each letter in our message the same number of steps around, we’ll vary it. So let’s agree that the first letter will rotate 3 places, the second by 18, and the third by 11: then the fourth by 3 again, the fifth by 18, the sixth by 11, and so on. If we encode the same message now, we get:
And so on. Suddenly that’s a lot more secure than our plain old Caesar Cipher! Congratulations: you just invented the Vigenère Cipher. Unfortunately for you, it’s almost 500 years old already. Even more unfortunately, it’s still not very secure. It’s fine for passing notes in class, but it won’t do for sending orders to your agent on the other side of the Iron Curtain!
How is a One-Time Pad different?
The “key” to the cipher we used above is 3, 18, 11, and the problem is that the key ends up being re-used (repeated) throughout the course of the message. If the message was the word “ELF” (encrypted to “HAQ”), and we agreed never to use that same key again, then anybody who intercepted the message – even if they knew we were using a Vigenère Cipher – wouldn’t know what we’d said, except to say that it had three or fewer letters. We could equally have said “MAN” (using the key 8, 17, 8), “EAT” (using the key 0, 17, 14), or “EGG” (using the key 0, 23, 1). If we ever used the same key – 3, 18, 11 – again, our code would become vulnerable to frequency analysis, which is a technique for working out what the key might be based on the likelyhood of particular letters or words (especially common ones) being used in combination.
It’s pretty easy to see how to fix this: all you have to do is to choose a key that is at least as long as the message you want to encrypt, and never reuse the key.
 This is how a one-time pad works. Suppose you and I agree a series of numbers, like this: 64191 25746 89891 93406 33604 89879. You keep a copy, and
I keep a copy, and we never tell anybody else those numbers, or the order in which they appear.
This is how a one-time pad works. Suppose you and I agree a series of numbers, like this: 64191 25746 89891 93406 33604 89879. You keep a copy, and
I keep a copy, and we never tell anybody else those numbers, or the order in which they appear.
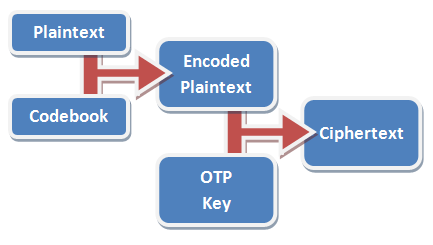
When I want to send you a message, I first convert that message into a series of numbers, using a codebook or codetable. In the example codetable below – which has been optimised for the English language – the most-commonly used letters are represented by one digit each, while less-frequently used numbers are represented by two digits. So the message “STEAL THE PANTIES” becomes 82832 17890 83752 80148 33282. It’s important to remember that this still isn’t encrypted; it’s just encoded: turned into a format suitable for encryption.
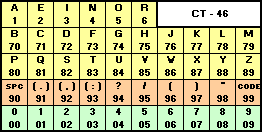
If we often talk about “panties” in our messages (and who doesn’t?), we might add that word to our codebook to make it faster to write: for example, we might assign it the code “11” – in the table above, the prefix “99” means “look it up in the codebook”, so instead of writing “panties” as “80148 33282”, we’d write it as “9911” – cold war spies had whole dictionaries of most-common words assigned to numbers to make them shorter to write out! That makes our message: 82832 17890 83752 99110. In this particular implementation, we add a padding zero to make it up to a nice round block of five digits.
Next, we encrypt the message using our pre-arranged secret key, 64191 25746 89891 93406 33604 89879. To do this, we just take each digit in the message and add it to each digit in the key, ignoring any “tens” column. So 8 plus 6 is (1)4, 2 plus 4 is 6, 8 plus 1 is 9, and so on, to get our encrypted message.
All you have to do to decode it is run the whole thing backwards. From each digit in the message, deduct the corresponding value in the key – if you get any negative numbers, just add 10 to them so that they’re not negative any more. Then run the resulting encoded number through your codebook to get back the secret message.
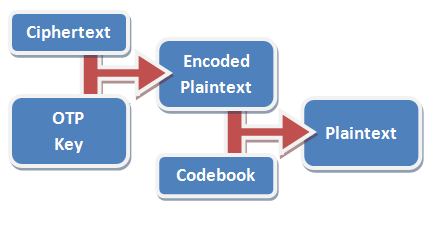 In practice, using a codebook is optional, but very-highly recommended. In the basic codebook I’ve provided with my implementation, the word
“condition” goes down from being “71547 23833 54” to just “99114 7”. A well-designed codebook will contain not only common words in your language, but anticipated words for the things
that you expect to talk about in your messages (like “MISSION”, “CAPTURED”, and – of course – “PANTIES”).
In practice, using a codebook is optional, but very-highly recommended. In the basic codebook I’ve provided with my implementation, the word
“condition” goes down from being “71547 23833 54” to just “99114 7”. A well-designed codebook will contain not only common words in your language, but anticipated words for the things
that you expect to talk about in your messages (like “MISSION”, “CAPTURED”, and – of course – “PANTIES”).
Messages encrypted using one-time pads are so secure that it’s safe to send the message itself completely in the clear, which is exactly what we used to do. Especially during the cold war, but still today (and increasingly), governments have been able to communicate with spies in foreign countries simply by broadcasting strings of numbers over conventional radio, from what are called numbers stations by radio enthusiasts (and also by conspiracy theorists, of course). Of course, nowadays it’s perhaps more-feasible to send many kinds of messages by e-mail – and there are a number of one-time pad systems optimised for fully-computerised use, although there exists a greater risk of being traced online than by simply tuning in a radio.
Now: go have a play!
Click the link – One-Time Pad Encryption/Decryption Engine in Javascript – to try out my one-time pad engine and encrypt and decrypt a few messages of your own. It’s quite deliberately written in a way which does not communicate with my server at all, once the program has downloaded (unplug your computer from your Internet connection if you like, and you’ll find that it still works), so I’m not able to see what you’re encrypting. You can use your own codebook if you like, and the entire source code for the page should be reasonably easy to read, if you’re that way inclined. Have fun!
However, you certainly shouldn’t actually use it for passing secret messages around: read the caveats below if you can’t work out why for yourself!
Further Reading
Kit and Fiona came down to Aberystwyth to visit the other week for the first time in ages, and – as Paul already wrote – they made the mistake of introducing everybody down here to the phenomenon known as geocaching.

For those who’ve not heard about it before, geocaching is often described as “a global game of hide & seek played using GPS technology”. Personally, I prefer Kit’s explanation, which is “using military satellites to find lost Tupperware”. Put simply, participants hide caches (often plastic stay-fresh containers) in interesting places around the globe, and publish the GPS co-ordinates online on websites like Geocaching.com, then other participants try to find them.

I suppose one could also describe the activity in the context of the pastimes it is most similar to. It could be described as being a little like rambling (although some caches are in urban locations and many are reachable by car), orienteering (but generally with less need to be able to triangulate points and read a map and more ability to use a GPS effectively and understand its limitations), hide & seek (finding things that have been hidden rather than people, of course), and one of any number of hobbies ending with “-spotting” (each geocache has a unique number, and many participants are trying to visit as many as possible, or to visit particular subsets of them).

I suppose another way of describing it might be in the context of the hot cold game, which you probably played as a kid: where while looking for something hidden, the hider calls out “warmer, warmer, colder, warmer again, hot!” as an indication to the seeker as to whether or not they’re on the right track. This analogy is particularly apt when one gets within a few metres of the cache, at which point GPS devices become almost useless at telling you which direction to go in (and of uncertain value at telling you how far away you are – when in a wooded area or surrounded by tall buildings, GPS can be thrown off by tens or even hundreds of metres).

Since Kit and Fiona’s visit, a number of us have jumped right in to geocaching. Paul, Ruth, Jimmy, Claire and I are all now represented on the site: as pacifist_049 (Paul), fleeblewidget (Ruth), JimEsk (Jimmy & Claire), and avapoet (me).

I can’t speak for all of these people, but there’s something about geocaching that’s really grabbed my interest. Since their visit, I’ve been out and found a number of the caches in and around Aberystwyth, and I’ve even hidden the first of my own. At the very least, I’ve been glad of the excuse to make better use of my bike, but more than that: I’ve been pleased to get around and see parts of the town and countryside that I don’t normally visit or look that closely at. Yes, even when I’ve ended up stuck up on a hill in the dark (that’ll teach me to go ‘caching after work in the short days of winter!).

Perhaps strangest, though, is my (so-far limited) experience of the local geocaching community. After you’ve visited a few sites around here you begin to notice patterns in the names of the people who’ve been there before you, and you start seeing the same aliases appearing again and again. And in a town the size of Aberystwyth, it’s invariably only a matter of time before you make contact with, well, everybody.

At the weekend I was in Morrisons, buying plastic tubs and other supplies with which to make caches – I suppose that in itself might have made me stand out: who goes to Morrisons to buy a stack of small Tupperware boxes and notepads small enough to fit inside them? – when a man come over to me. He looked at me, as if trying to work out where he knew me from, and then looked down at my hands and saw what I was carrying. “Avapoet?” he asked. “Treedoctor2000?” I replied. So there we have it, I’m officially part of the local geocaching community, and I didn’t even mean to.

So there we have it, a glowing review for a fun new activity that if you haven’t tried, you ought to. If you own a GPS or even a modern mobile phone or even just a portable SatNav system, you’ve probably got all you need to get started, and with almost a million caches around the globe, there are sure to be a few near you. So if you were waiting for my approval before you went and did so, here it is.
Now get away from the computer and go do something outdoors!
Further Reading
This checkin to GL3C41ZC Alphabet Series - C reflects a geocaching.com log entry. See more of Dan's cache logs.
Changed my mind about waiting until the morning and set out just after midnight, as one can get away with when looking for urban caches. FTF! Found it without even pulling out my GPS, but did have to look inconspicuous for the passing muggles (although they looked too drunk to be paying attention anyway). Took the compass (thanks!), left a candle. TFTC!
This checkin to GC23N8B Alphabet Series - C reflects a geocaching.com log entry. See more of Dan's cache logs.
I’ll go hunt for this tomorrow, probably (I’m very familiar with the area in question: it’s right next to where I work), but based on the map this cache is by the River Rheidol, not the Ystwyth, which (confusingly) is actually a little further South. Just thought you ought to know!
This checkin to GL3C1T19 Pen y Bwlch reflects a geocaching.com log entry. See more of Dan's cache logs.
I remember that when I was first a student at Aberystwyth I’d often come up here for a walk, and I never got out of breath then! ,Of course, we’re a decade later on, now, and – in my defence – I jogged most of the way up the steep, slippery slope from Trefechan beach to the plateau in a folly attempt to reach the cache before the sun set. More fool me! By the time my GPS said I was within even 200 metres it was near pitch-black, the little dwindling light in the sky dimmer by far than the streetlights of the town far below.
Found the cache without too much difficulty, but had quite a lot of difficulty extracting it: here’s a tip: if, like me, you have big hands, bring along a friend with smaller fingers. That’s all I’m saying (I had to manufacture some artificial “tiny fingers” out of sticks; yes, in the dark).
Anyway, in short – TFTC, it’s been years since I’ve been up here and I’m thankful for the excuse to have returmed. Now all I have to do is find my way down again without going over a cliff!!! (if you never see my log another cache, at least you have my last known coordinates)
UPDATE: made it down safely, now enjoying a (well-earned) pint of beer!
This checkin to GL3C1F9C Rainbow Series Violet #2 reflects a geocaching.com log entry. See more of Dan's cache logs.
TFTH. Finding this cache was easier than hiding it again afterwards – I got a splinter! Left something almost-violet, took nothing.
[This entry was edited by avapoet on Saturday, February 27, 2010 at 9:53:52 AM.]
This checkin to GL3C06F1 Cwm Rheidol - Dau Bont reflects a geocaching.com log entry. See more of Dan's cache logs.
Feet got a little wet: if I’d have read the hint first I’d have known better! Note: no pencil in cache, make sure you bring your own! TFTC.
This checkin to GL3BZYF3 Bonus Cache (Cwm Rheidol Expedition) reflects a geocaching.com log entry. See more of Dan's cache logs.
Excellent cache, great hiding place. took the travel bug to move him along. Will swing by to drop something off next time I’m nearby. Good luck to treedoctor2000 and fb_n_tw, who must soon be on their way here!
EDIT: dropped off a fire engine!