The Register have a report on a survey of the musical tastes of IT specialists, by profession. If you’re a geek, date a geek, live with geeks, or whatever, it’s worth a look.
Tag: technology
Reb, Hell, And Unreal Tournament 2004
After I saw Faye’s weblog post about her own design for hell, I couldn’t help but leave an anonymous comment. If you’ve ever met Reb, my ex-girlfriend from a few years back, perhaps you’ll appreciate.
In other news, I spent far too much of the weekend playing the demo of Unreal Tournament 2004. I haven’t had so much fun with the demo of a computer game since about 1999 (I never have time for demos any more). Wow… it really is something stunning. They’ve really put a lot of work into making it accessible by anybody, too – the hardware specifications aren’t so horrible, and it’ll run on Windows, Linux, or MacOS X! Hell; it doesn’t even require a 3D card (although I wouldn’t like to try it without one!). It’s a doddle to get it running on a network (Bryn and I had a couple of LAN games – driving a tank right into an enemy base with one of you sat on the top with a minigun is sooo much fun), it’s fast and furious, and relies heavily on teamwork. It’s just fab. Have ordered a copy from Amazon.
Scatmania, Version 2
Welcome to Scatmania, Version 2!
After my disasterous data loss the other day, I decided to take the oppertunity to redesign Scatmania into something altogether better-suited to the purpose (i.e. doesn’t use a silly flat-file system). And here it is (well; unless you’re reading this through LiveJournal).
I’ll be graduating this afternoon, which will mostly involve standing around in silly robes while a man talks bollocks in Welsh. After this, I’ll be going out for a meal with my folks, who’ll be visiting for the occassion.
On an unrelated note, does anybody want to join Claire, Bryn, Paul and I on a trip to Alton Towers, some weekday during September (taking advantage of the cheap rates and lack of schoolchildren that’s available at that time of year)? Date to be confirmed, but if you want in, drop us a message or leave a comment.
Some People Should Not Be Allowed On The Internet
In related news, I hear that some folks have been arrested on suspicion of being behind the Half-Life 2 code thefts. Maybe Valve were waiting for the arrest to be made so they could get their code back. =o)
The Importance Of A Sensible Patent System In Europe
If Haydn had patented “a symphony, characterised by that sound is produced [ in extended sonata form ]”, Mozart would have been in trouble.

Click Here — Sign The Petition
Just thought I’d share that link with you. This is something which could eventually affect the way we all use computers. To those of you who don’t recognise these images or have no idea what I’m on about, I urge you to read about the issue of software patenting in Europe.
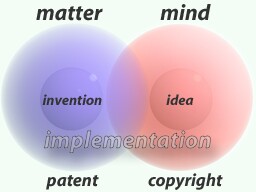
Thanks for listening.
You Know Your Program Is Convoluted When…
…the client calls up and says, “I’m not sure if this is a bug… or a feature… but -”
Bovini is fucking scary these days.
How To Use SSH Tunnelling To Allow Services To Pass Through A Firewall
[this post has been partially damaged during a server failure on 11 July 2004; with the exception of the images, it was recovered on 13 October 2018]
Paul has been stuck with a problem of late – he’s now living in university accomodation, and he’s found that he can’t connect through the university firewall to his external mail server. I advised him that it’s possible to set up an ‘SSH Tunnel’ (through central.aber.ac.uk) to fix this problem, but he hasn’t met with much success (see his blog entry for more details). In any case, here’s my investigation (and solution) to the problem.
How To Use SSH Tunnelling To Allow Services To Pass Through A Firewall
In my example, I’m going to try the opposite to what Paul is trying to achieve. I’m going to try to allow my POP3 e-mail client to get access to the university e-mail server
(pophost.aber.ac.uk). As things stand, this server is on the other side of the university firewall, and is inaccessible from outside. The server central.aber.ac.uk, however, is
accessible from both sides of the firewall. So what I’ve got is this (yes, I know that this is a gross oversimplification):

As you can see, connecting from my home PC is futile:
C:\Documents and Settings\Dan>telnet pophost.aber.ac.uk 110
Connecting To pophost.aber.ac.uk...Could not open connection to the host, on por
t 110: Connect failed
But if I SSH-in to central.aber.ac.uk…
central:~ $ telnet pophost.aber.ac.uk 110
Trying 144.124.16.40...
Connected to pophost.aber.ac.uk.
Escape character is '^]'.
+OK mailsplit Oct 2000 ready
So, what I need to do is to tell my SSH client to connect to central.aber.ac.uk, and forward specific traffic through the firewall to the mail server. Here’s what I needed to know:
(a) A free TCP port number on my own computer from which I can virtually ‘pipe’ the connection. Most numbers over 1024 are fine. I chose ‘9110’.
(b) The name of the mail server – ‘pophost.aber.ac.uk’.
(c) The TCP port to which I wanted to connect – the standard port for a POP3 mail server is ‘110’.
(d) My user name on a server which: (1) I can connect to; (2) can connect to the server specified in (b). It happens to be ‘dlh9’.
(e) The name of the server specified in (d) (i.e. ‘central.aber.ac.uk’).
(f) My password on the server. Like I’m going to tell you that.
The syntax is:
ssh -L (a):(b):(c) (d)@(e)
I’m using the non-commercial version of SSH Secure Shell Client, so here’s what happens:
C:\Documents and Settings\Dan>"\Program Files\SSH Secure Shell\ssh2.exe" -L 9110
:pophost.aber.ac.uk:110 dlh9@central.aber.ac.uk
dlh9's password:
Authentication successful.
At this point, I’m ready to go. Look what happens when I connect to port 9110 on my own computer, now…
C:\Documents and Settings\Dan>telnet localhost 9110
+OK mailsplit Oct 2000 ready
I could simply point my e-mail program at the ‘mail server’ at localhost:9110, and I’d be able to collect my university e-mail (so long as my SSH connection remained open).
Hopefully this guide will help some folks out there who are struggling with this kind of thing, and in particular, help Paul.
My Very First Operating System
[this post has been partially damaged during a server failure on Sunday 11th July 2004, and it has been possible to recover only a part of it]
[more of this post was recovered on 13 October 2018]
I’ve just written my very first Operating System! And I’m putting it here, online, so that you can give it a go if you like. And no, you don’t need to install it – just put it on a floppy disk and try it from there (no, you can’t boot it from a CD yet)!
Don’t expect too much. There’s no user interface (not even a command line). All it is is a bootloader and a kernel that ‘displays pretty squares’ (I stole the ‘pretty squares’ code from somebody else – my Assesmbly needs some work!).
Hardware Requirements
386SX/25MHz or faster processessor
520K or better memory
Floppy disk drive
Instructions For Use
1. Download the floppy disk image file [34K]
2. Download and install WinImage 6.1 (this program lets you write floppy disk image files to
floppy disks).
3. Open the image file in WinImage, insert a floppy disk, and select “Format And Write Floppy Disk” from the “Disk” menu. The Operating System will be written to the floppy disk.
4. To run it, you need to reboot your computer with the floppy disk in the drive. If this doesn’t …
I AM Scared Of Bootloaders
I’ve spent the evening looking at bootloader source code (small programs, crucial to every Operating System, which do the first fundamental steps towards loading the kernel, the ‘core’ of the OS). Just to show you quite how scary this stuff is, here’s a snippet of code to “stop the floppy drive motor from spinning”:
mov dx,3F2h
mov al,0
out dx,al
Remember Microsoft vs. Netscape?
Then you’re old enough to appreciate this: OSNews is running an article about the upcoming fight between Google and Microsoft. Where the Netscape/Microsoft battle involved web browsers, the weapons of the Google/Microsoft battle will be search engines and e-mail services.
If you’re confused as to how companies can be fighting by trying to increase the market share of their free product, read the article.
EU To Use Quantum Crypto-Key Passing To Beat ECHELON
[this post has been partially damaged during a server failure on Sunday 11th July 2004, and it has been possible to recover only a part of it]
[further parts of this post were recovered on 13 October 2018]
Now here’s an interesting article [security.itworld.com]. It seems that the European Union is investing €11 million over four years into developing a secure communication system based on quantum cryptography.
For those of you not in the know, quantum cryptography (for passing crypto keys) works like this:
Quantum Cryptography For Dummies
- Alice wants to send Bob secret message, confessing her undying love, but doesn’t want anybody else to know how she feels.
- She fires some photons out of a special tube, so that some of them spin in different directions.
- Numbers are assigned to the different directions of spin, and she multiplies these together – along with a few prime numbers, for good measure – to get a Really Big Number.
- Then, Alice does some clever sums on the letters in her love letter, using the Really Big Number.
- Alice posts the first line of the new love letter to Bob (the line that says “Dear Bob,”). This is known as the ‘message header’. If Bob sends a message back saying that he got this, Alice will send the rest of…
Half-Life 2 To Be Released As Twin-Pack
Yay! Take a look at this piccy (especially you, Paul).
Common OS Myths Debunked
[this post has been partially damaged during a server failure on Sunday 11th July 2004, and it has been possible to recover only a part of it]
In this era of pro-Linux and pro-Windows hoo-hah, it’s good to see an article who’s writer really has his head screwed on: Common OS Myths Debunked is a wonderful piece; go read it.
Linux is not the answer!
Windows is not the answer either!
Don’t even get me started on MacOS…
Operating…
New XML-Based Markup Language: MRML
Everything You Ever Wanted To Know About The ID Card But Were Afraid To Ask
The Register are running an article about the new UK ID card, and what it all means. They’re always a great source of information on such things, if slightly cynical… and this document is no exception. Go read it. Then throw rocks at Mr. Blunkett. <grin>


