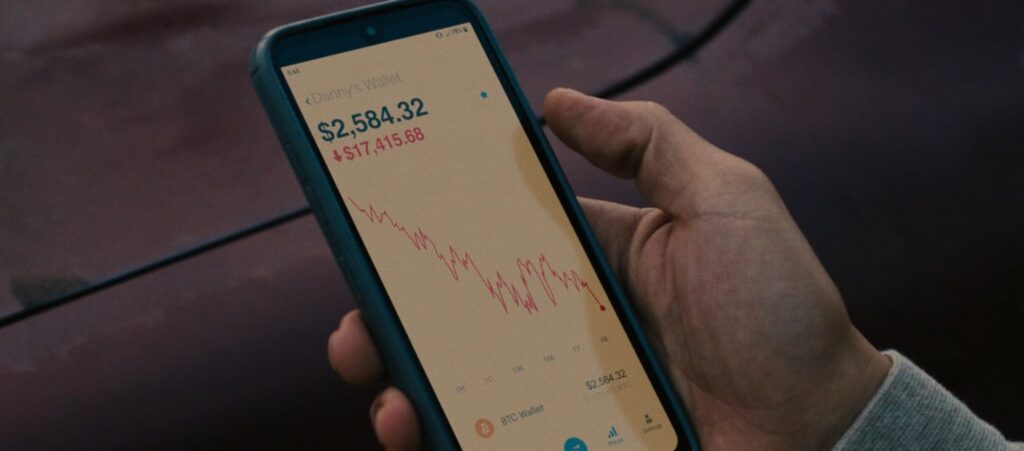
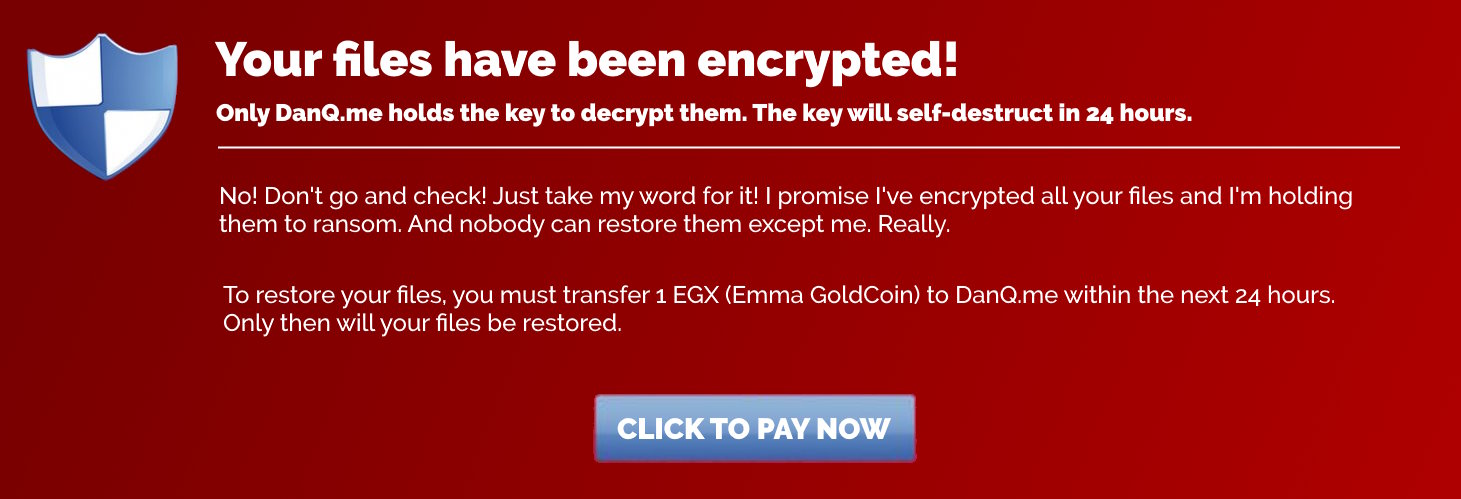
It’s a common complaint that cryptography is too hard for regular people to understand – and that all our current cryptographically secure applications are designed for cyborgs and
not humans. While the latter charge may well be correct, I argue that the former most certainly isn’t, because we have been teaching children the basic security principles behind
asymmetric cryptography for probably thousands of years.
What am I talking about? A fairly tail called Rumplestiltskin, which is actually about bitcoin!
You probably heard this fairly tale as a child – but let me refresh your memory.
There is a miller, who drunkenly brags that is daughter can spin straw into gold.
probably, he was posting about his half baked cryptocurrency ideas on
bitcointalk, and creating money “gold” from pointless work “spinning straw” sounds A LOT like bitcoin mining.
Anyway, the king is very impressed with his story.
the king is a venture capitalist?
And wants to see a demonstration, oh and if it doesn’t work he will cut off both their heads.
I have not heard about venture capitalists being quite this evil, but it seems some of them are into this
medieval stuff
Of course, the miller and his daughter don’t actually have the ability to create gold by magic, so they are in big trouble! but just then a magic imp appears.
a hacker, who understands cryptography
The imp says he can spin straw into gold, but for a price: the daughter’s first born child.
in the modern version he wants her naked selfies
It’s a terrible deal, but the alternative is death, so they reluctantly accept. The imp spins straw into gold in 3 increasingly dramatic episodes.
The kind is satisified, and marries the daughter, making her queen.
their startup is aquired
One year later, the first child is born. The imp returns demanding his prize. Because they love their baby, the King and Queen pleads with the imp to get out of the deal. They offer
him all their riches, but the imp is not interested! Desperately, they ask is there any other way? any at all? The imp replies, “Of course not! not unless you can guess my True
Name”
the true name is actually his private key. If they can guess that, the hacker looses his magical power over them
“Okay I will try and guess your name” says the Queen. The imp just laughs! “you’ll never guess it!” “but I’ll give you three days to try!”
The imp skips off into the forrest, and the queen trys to think of his name for 3 days… but can’t figure it out.
The queen trys to brute force his private key. but there is not enough compute in the entire kingdom!
But then, the a messenger is travelling through the forrest, and he happens past a strange little man, dancing around a camp fire, singing:
ha ha ha!
te he he!
they’ll never guess my private key!
just three days! not enough to begin,
to guess my name is rumplestiltskin!
Being a messenger, he had a good memory for things he heard. When he arrived back at the castle, he mentioned the curious story to the queen.
the hacker had been careless with his private key
When the imp arrived in the morning, the queen greeted him by name. He was furious! He stamped his foot so hard the ground split open and then he fell into the gaping hole, never to
be seen again. The king, queen, baby lived happily ever after, etc, etc.
they stole all his bitcoin
The simularities between this fairly tale and cryptography is uncanny. It has proof of work, it has private keys, it has an attempted brute force attack, and a successful (if
accidental) end point attack. The essential point about your private key is captured successfully: the source of your magic is just a hard to guess secret, and that it’s easy to
have a hard to guess name, but what gets you in the end is some work around when they steal your key some other way. This is the most important thing.
It’s not a talisman that can be physically protected, or an inate power you are born with – it’s just a name, but it must be an ungessable name, so the weirder the better.
“rumplestiltskin” is the german name for this story, which became wildly known in english after the brothers grim published their collection of folktales in the early 19th century,
but according to
wikipedia there are versions of this story throughout the europe, and the concept that knowing the true name of a magical creature give one power over it is common in mythology
around the world.
How did the ancients come up with a children’s story that quite accurately (and amusingly) explains some of the important things about asymettric cryptography, and yet we moderns
did not figure out the math that makes this possible this until the 1970’s?
Since the villian of the story is magical, really they have chosen any mechanism for the imps magic, why his name? Is this just a coincidence, or was there inspiration?
The astute reader has probably already guessed, but I think the simplest (and most fun) explaination is the best: extraterrestials with advanced cryptosystems visited earth
during prehistory, and early humans didn’t really understand how their “magic” worked, but got the basic idea
To be continued in PART 2…