With my day job at SmartData I’ve recently been doing some work for a client, transporting their data from the Microsoft SQL Server that back-ends their desktop application and converting it to a different schema on a different database for a new, web-based application. Because there’s quite a lot of data, the schema are quite different, and the data needs to be converted in a “smart” way: I’ve written a program to help with the task.
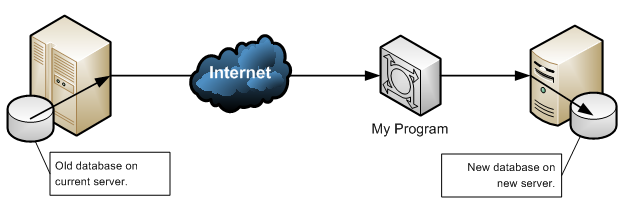
Unfortunately, it’s a slow process to move all of the data over. So, to test my program as I continue to develop it, I thought it might be useful if I could take a copy of the “live” database to somewhere more local (like my computer). This would remove the overhead of going through the Internet each time, and reduce the run time of the program significantly – an important consideration during its ongoing development.
Unfortunately, a quirk in the way that Microsoft SQL Server works is that the backup file I can make (ready to restore onto my computer) doesn’t appear on my computer, but appears on the old server. And I don’t have a means to get files off the old server. Or do I? I have a username and password: I wonder if there are any other services running on the server to which I might have access. To find out, I use a program called Nmap to try to get a picture of what services are running on the server.
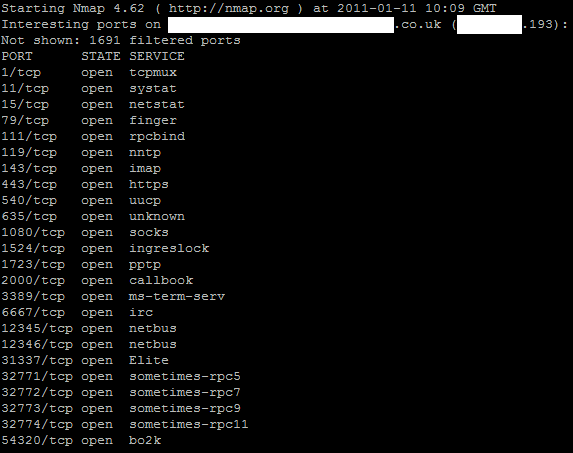
And that’s when I realised that something might be wrong. For those of you who aren’t inclined toward understanding the ins and outs of network security, the screenshot above should be considered to be more than a little alarming. There’s pretty obvious and clear signs that this computer is infected with Trinoo, NetBus, Back Orifice, and quite probably other malware. It’s almost certainly being used as part of denial of service attacks against other computers, and could well be stealing confidential information from our client’s server and the other computers on their network.
How have things gotten so out of control? I’m not sure. I’ve never seen such a rampant runaway set of infections on a server system before. Computers belonging to individuals, especially individuals inclined to installing BonziBuddy, Smiley Central/Cursor Mania, and so on, are often littered with malware, but one would hope that a server administrator might have a little more wisdom than to let unauthorised code run on a server for which they were responsible. At the very least, a Windows-based, Internet-accessible server ought to be running a strict firewall and antivirus software (virtually all antivirus software would have detected all three of the infections I’ve named above).
Just about anybody can get onto the ‘net, these days, and I can just about forgive a regular Jo who says says, “I don’t know anything about computers; I just want to play FarmVille.” It’s disappointing when they end up inadvertently helping to send email advertising “$oft C1ALIS tabs” to the rest of us, and it’s upsetting when they get their credit card details stolen by a Nigerian, but it’s not so much their fault as the fault of the complexities they’re expected to understand in order to protect their new computer. But when somebody’s running a service (as our client is paying for, from a third-party company who’s “managing” their server for them), I’d really expect better.
The Bit for the “Regular Jo”
And if you are a “regular Jo” on a Windows PC and you care enough to want to check that you’re part of the solution and not part of the problem, then you might be interested in a variety of free, trusted:
- Anti-virus software (essential)
- Adware/spyware removal tools (useful if you routinely install crap downloaded from the web), and
- Firewall software (essential if you connect “directly” to the Internet, rather than via a “router”, or if you’re ever on networks on which you can’t trust the other network users – e.g. free wi-fi access points, shared Internet connections in student houses, etc.)
Edit: And don’t forget to regularly install your Windows Updates. Thanks to Gareth for the reminder that regular Jos should be encouraged to do this, too.